Connected Apps for Organization Administrators
As an organization administrator at the root organization or business group level, you are the only user who can view and manage connected apps in Access Management. You can use authorization policies to dictate which apps are authorized to access user data, and you can add apps to an allowlist.
Connected App Ownership
Connected app ownership gets transferred to the root organization owner when the user who created the connected app:
-
Is deleted
-
Is removed from the root organization
-
Loses administrative privileges over the organization
To maintain security, manually rotate the client secrets of all connected apps in the organization after the transfer. For more information about how to manually rotate client secrets, see Modify the Client Secret for a Connected App.
You can also reset client secrets programmatically using the Access Management API.
Manage Owned Apps
To maintain security, you can view and manage connected apps only if you have the Organization Administrator permission in the root organization or in the business group where the connected app resides.
To manage your connected apps:
-
Navigate to Access Management and select the Connected Apps tab.
-
Add and edit apps in the Owned Apps section.
-
Manage app access in the Authorizations section.
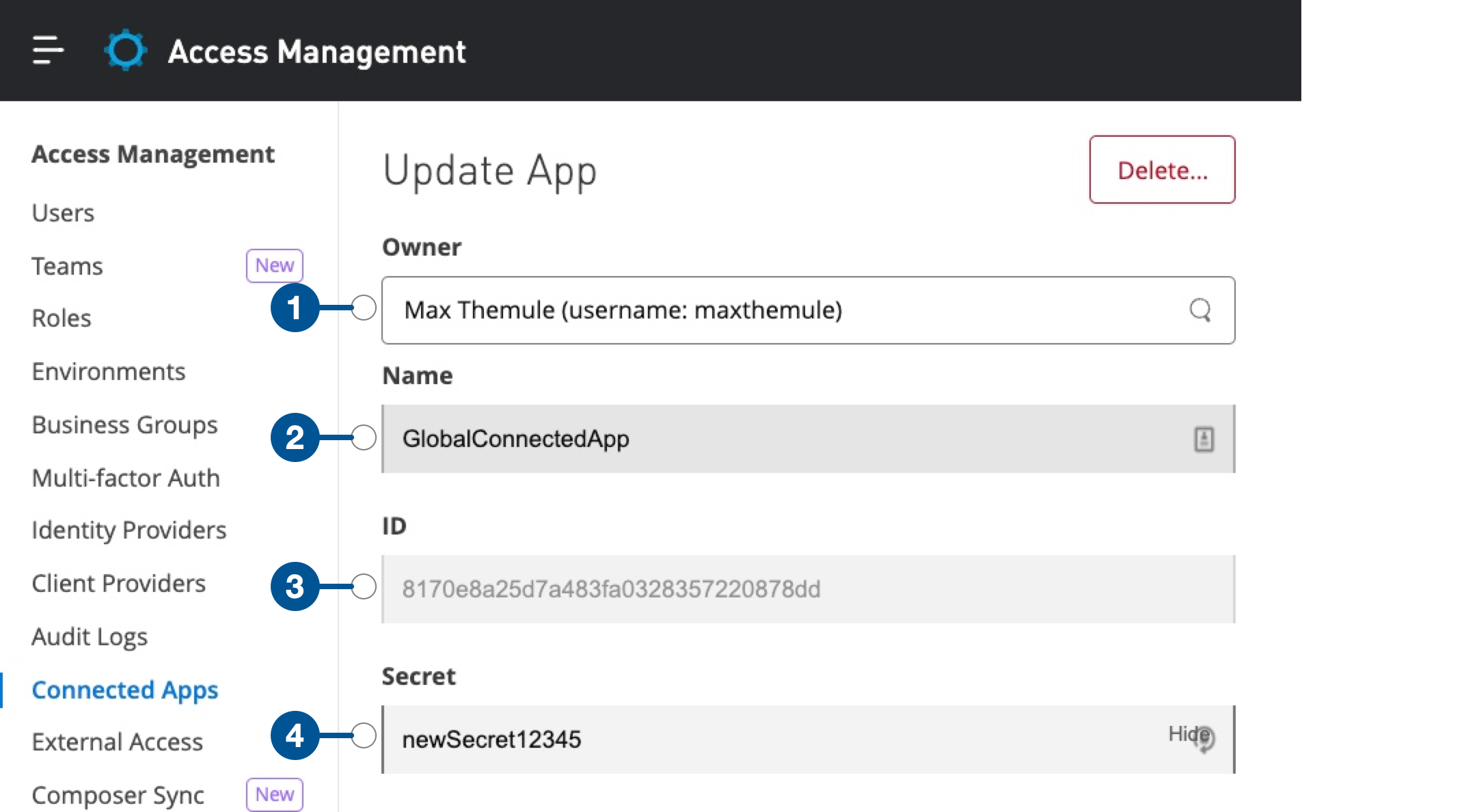
Edit the App Owner
Organization administrators can edit the owner of the connected app and transfer the ownership to other administrators:
-
In Access Management > Connected Apps > Owned Apps, click the app name.
-
Make the changes and click Save changes.
Modify the Client Secret for a Connected App
-
In the Access Management navigation menu, click Connected Apps.
-
Click a connected app from the list to enable edit mode.
-
In the Secret field, enter a secret of your choice.
-
Click Save.

| 1 | Name and username of the owner of the connected app |
| 2 | Name of the connected app |
| 3 | ID of the connected app |
| 4 | Client secret of the connected app |
View Authorizations
-
In the Authorizations tab, select the app.
-
Click the more actions menu (…) for the application and select Show details.
Revoke Authorization
When you revoke an app’s access, the app’s OAuth 2.0 access tokens and refresh tokens are revoked, and the app can no longer access user data. This action can’t be undone.
-
In the Authorizations tab, select the app.
-
Click the more actions menu (…) for the selected application and select Remove.
-
Click Remove.
Configure Authorization Policies
You can configure one of these types of authorization policies for your users:
-
Unrestricted
Organization members can authorize any connected app to act on their behalf.
-
Restricted
Only connected apps that are added to an allowlist by an administrator are authorized by organization members to act on their behalf.
By default, the Unrestricted policy is enabled. If you change the policy to Restricted, the application allowlist is enabled, and all existing application authorizations are added automatically.
When using the Restricted policy, you can disable auto-approval of all internal apps, in which case you must add each internal app to the application allowlist like any other connected app.
Application Allowlist
When the allowlist is enabled, organization users can use only applications that are on the allowlist. If a user attempts to authorize an app that’s not on the allowlist, they are prompted to contact their organization administrator.
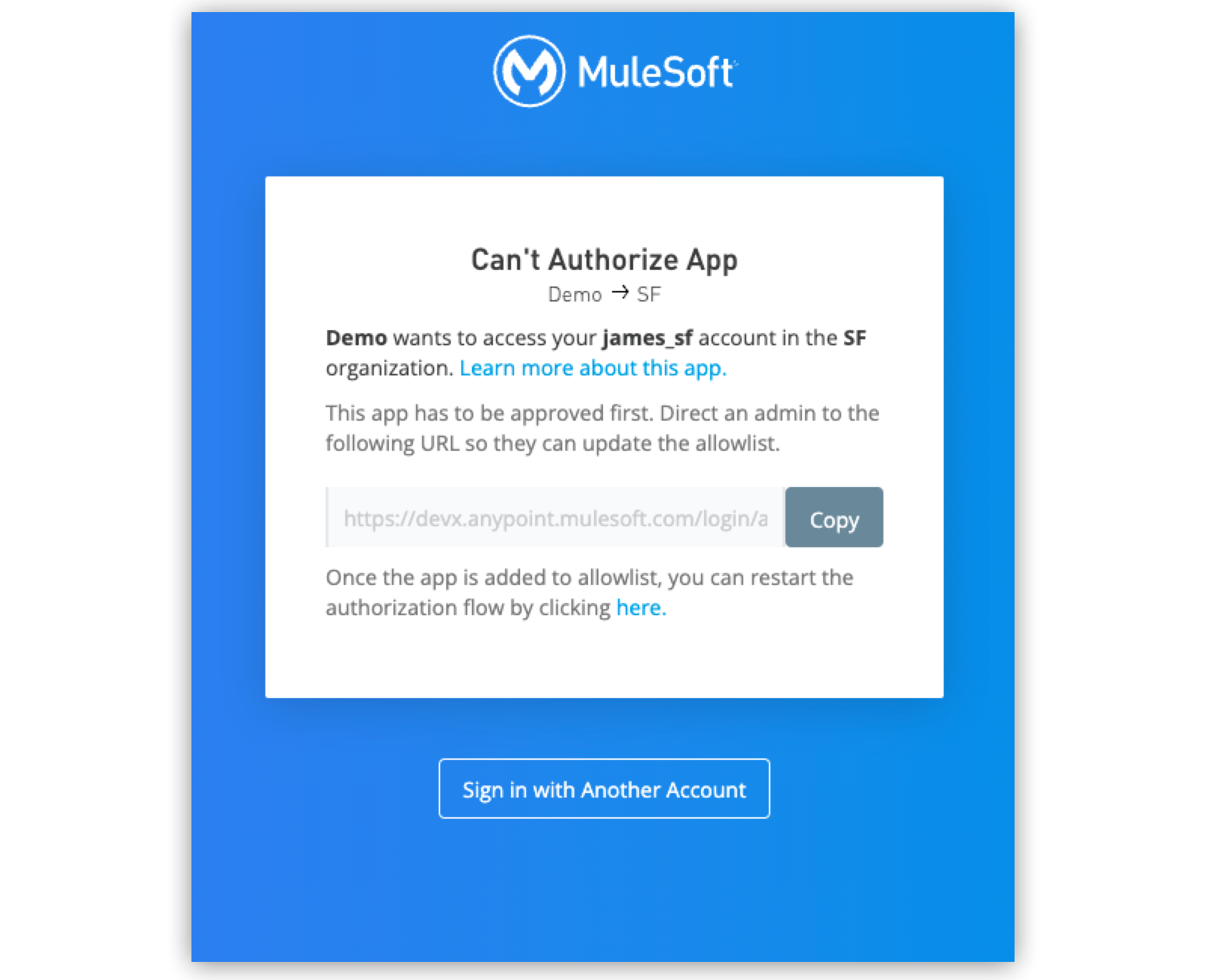
Organization administrators are able to add the app to the allowlist by following the link given to them by the end user.

Sometimes, apps start to ask for additional scopes. This happens when app developers add new features to their products and need to access more data in your organization. Previously allowed apps must be added to the allowlist again with the new set of scopes before your users can grant those additional scopes to the app.
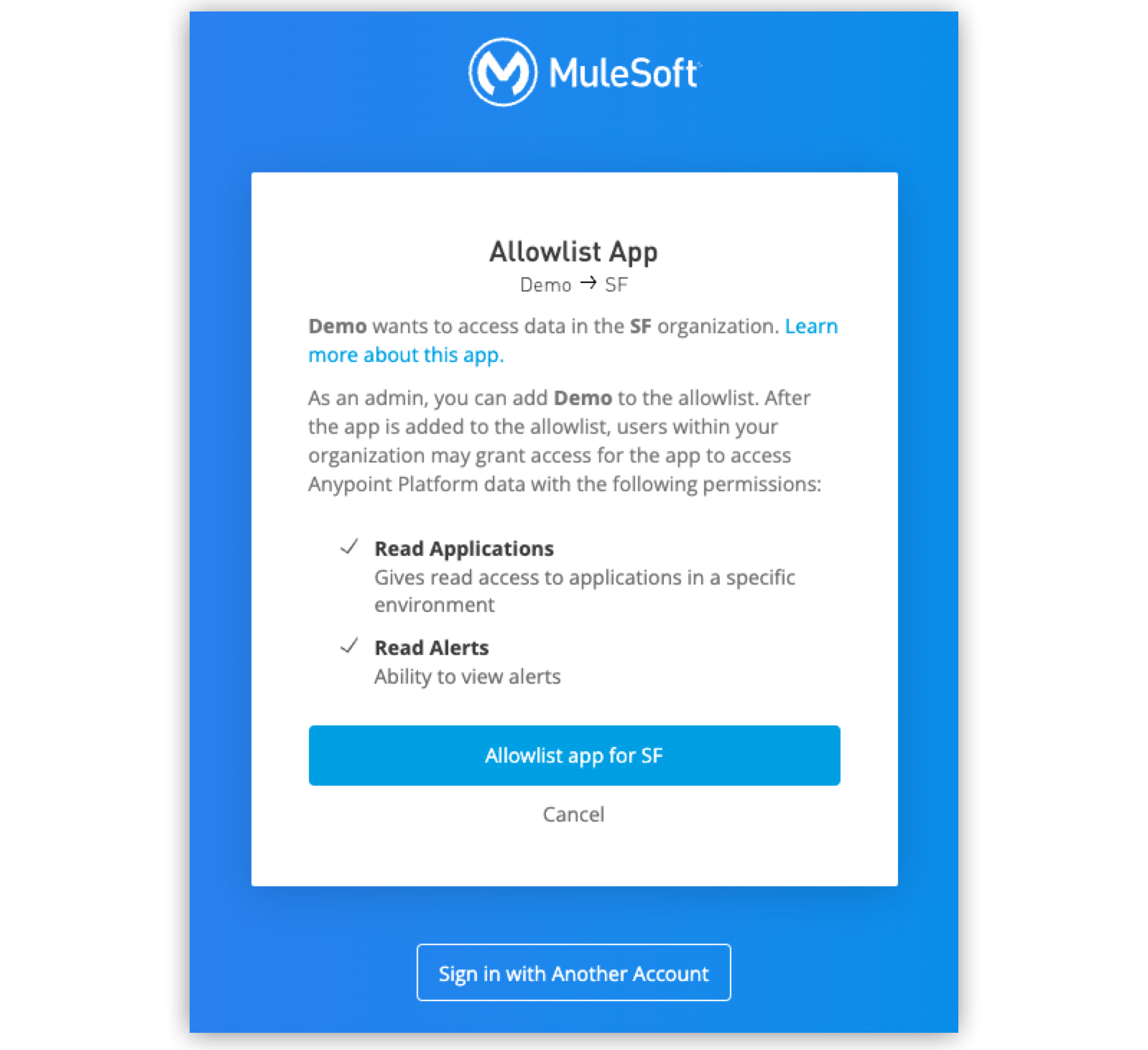
Existing authorizations continue to work if the app is not added to the allowlist again. New authorizations using the already-allowlisted set of scopes are also allowed. Apps that remove scopes do not need to be added to an allowlist again.
|
Applications created by users in the same organization are marked as internal apps and do not need to be allowlisted manually. |
Root Organization and Business Groups
By default, connected apps are configured at the root organization level, not at the business group (sub-organization) levels.
When you create a connected app to act on its own behalf using client credentials, you can choose which root organization or business groups to enable it in after you choose scopes.
A connected app that acts on behalf of a user receives its own access and permissions based on the scopes, organizations, and business groups to which the user has access.



