Secure Storage Overview
Anypoint Studio 7.10 and earlier versions stored the information of authenticated users in the workspace, meaning that you could have different authenticated users per workspace.
Studio 7.11 and later introduce Secure Storage, provided by Eclipse to encrypt and save your credentials.
Studio provides a main password provider that automatically generates a main password for all your user credentials. When adding a new credential, Studio uses your main password to encrypt and save that credential into a secure storage file in your file system.
The architecture of Secure Storage enables user authentication to be shared across all Eclipse-based workspaces and Anypoint Studio instances.
Main Password Providers
The available main password providers depend on your operative system. Studio assigns a priority to the available main password providers and enables you to choose which one to use. By default, Studio assigns a higher level of priority to the password provider that uses your OS’s underlying capabilities to generate and encrypt your main password.
When adding a new credential to Studio, it automatically uses the main password generated by the password provider with the highest priority to encrypt your credential, and stores it in a secure storage file located in your filesystem.
- Windows Integration (64 bit)
-
Available on Windows. This provider creates and encrypts a main password based on your Windows login information and stores it in secure storage. Windows Integration then uses this main password automatically to decrypt your credentials.
- OS X Keystore Integration
-
Available on macOS. OS X Keystore Integration uses a random value that is stored in the Keychain Access app. This provider uses the main password automatically to decrypt your credentials.
- Linux Integration (64 bit)
-
Available in Linux. This provider uses a random value and relies on the
libsecretlibrary that must be present and working on your Linux distribution. This provider uses the main password automatically to decrypt your credentials. - UI Prompt
-
Available in Windows, macOS, and Linux. This provider prompts you to create a main password and uses it to encrypt your credentials. This provider requires you to enter your main password every time you open Studio.
When you add a new credential for the first time, Studio notifies you that a new main password has been created. Additionally, Studio prompts you to create two password hints to use in case you forget your main password. The password hints are security questions that you must treat as a second password. If you lose your main password, your password hints are the only other method to recover your credentials.
Each provider supplies its own main password. When you use a provider to encrypt a new credential, you can only use that provider to recover the encrypted credential.
After a main password is created, Studio caches the main password until it is closed, or you manually clear the password from Studio cache.
Secure Storage File
This file holds all your user credentials in an encrypted form. By default, the secure storage file is located in $HOME/.eclipse/org.eclipse.equinox.security/secure_storage and is shared across all Eclipse-based workspaces and Anypoint Studio instances.
Update the Main Password
You can change the main password for a particular provider. When changing a main password, all the encrypted data by this provider is re-encrypted with the new main password.
Before you Begin
To avoid decryption issues, ensure that all other instances of Anypoint Studio and any other Eclipse-based application are not running.
To regenerate your main password:
-
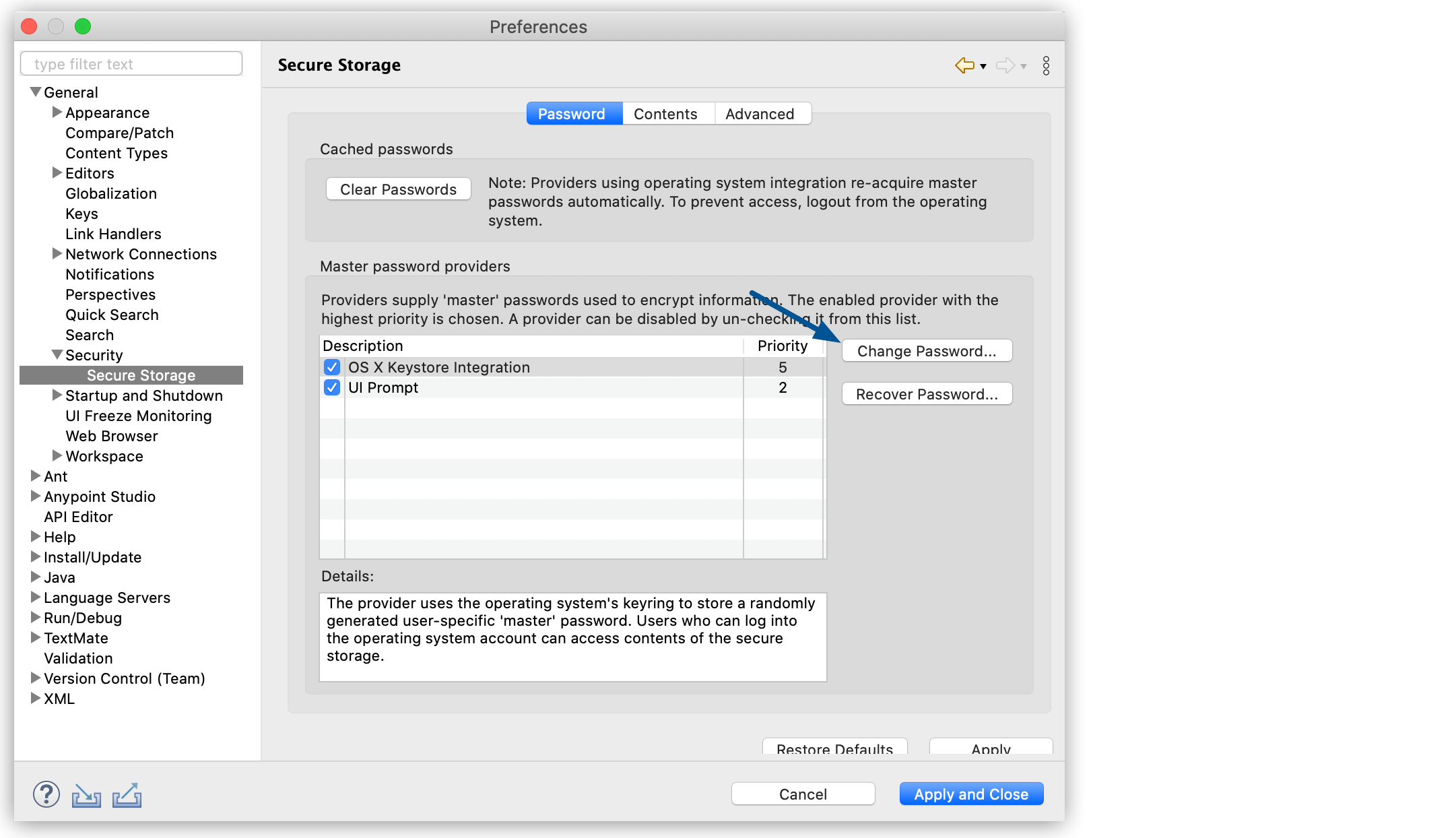
Navigate to Preferences > General > Security > Secure Storage.
-
Select Change Password…:

-
When Studio prompts you to create password hints, select Yes:
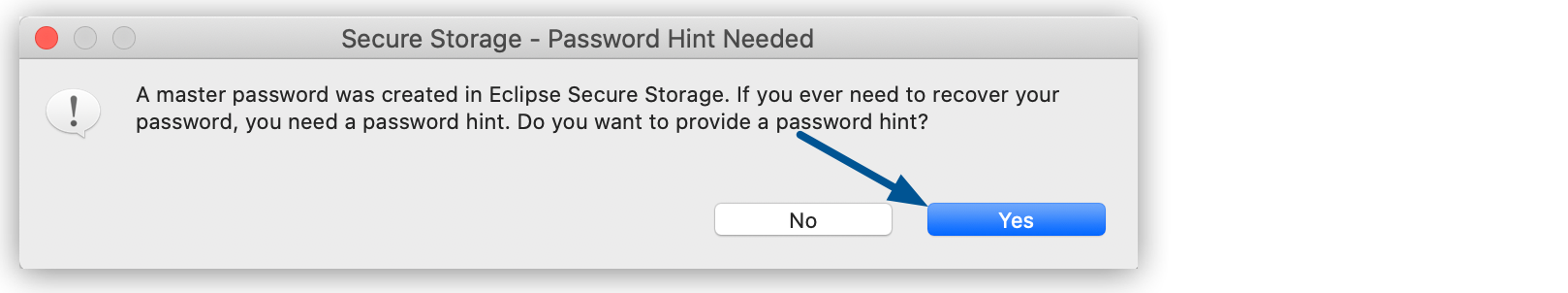
If you don’t supply new password hints, then the existing hints persist, referencing the existing main password, and you will not be able to recover your new main password.
-
When Studio confirms that the password is successfully updated, select Apply and Close.
Customize the Location of the Secure Storage and Password Files
To change the location of the password and secure storage files:
-
Locate your
AnypointStudio.inifile:-
In Windows:
-
Go to your Anypoint Studio installation directory.
-
-
In macOS:
-
Go to your
/Applicationsfolder, right-click theAnypointStudiopackage, and select Show Package Contents. -
Go to
Contents>Eclipse, and open theAnypointStudio.inifile.
-
-
In Linux:
-
Go to
/usr/lib/anypointstudio/anypointstudio.ini.
-
-
-
Add the following options to bypass the password provider mechanism:
-eclipse.keyring <file_path> (1) -eclipse.password <file_path> (2)1 Configures the location of the Secure Storage file. 2 Configures the location of the password file, which Studio uses as the main password.
| You can only decrypt your credentials with the same password file used to encrypt them. |
Decryption Errors
No Password Provided
Exception: org.eclipse.equinox.security.storage.StorageException: No password provided
This error occurs when Studio loads and caches the main password for the provider and tries to decrypt a value that was encrypted with another main password.
This happens when a user of one instance of Studio or another Eclipse-based application changes the main password at the same time that a user in another instance of Studio saves a new credential using the previously cached main password.
Given Final Block Not Properly Padded
org.eclipse.equinox.security.storage.StorageException: Given final block not properly padded. Such issues can arise if a bad key is used during decryption..
This error occurs when the currently cached main password cannot decrypt a value because that value was encrypted using the previously cached main password.
This happens when a user using one instance of Studio or another Eclipse-based application changes the main password, and another instance of Studio or the application attempts to read encrypted values by using the previous cached main password.