About Provided Policies
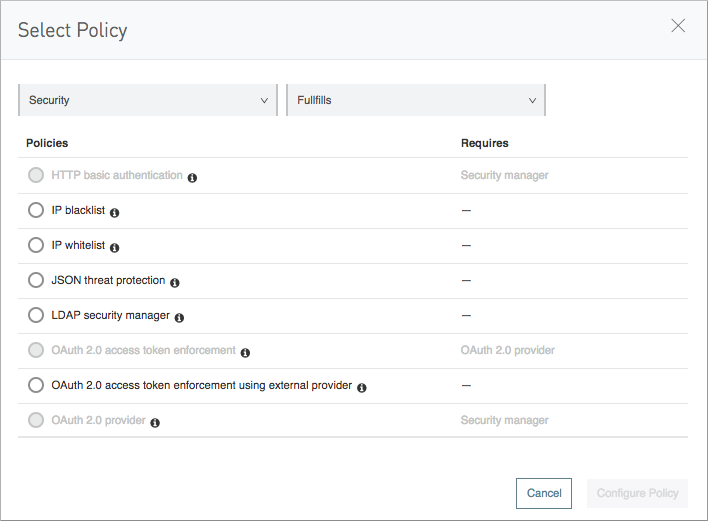
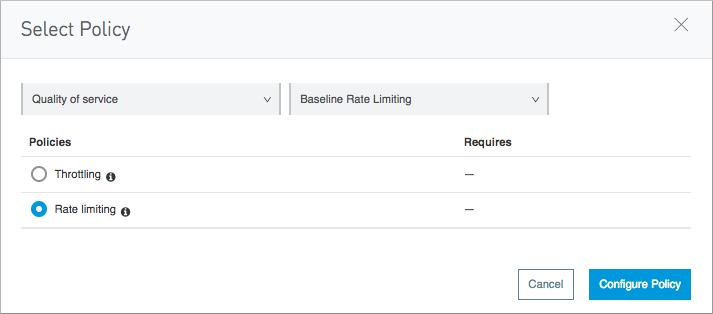
In the process of applying a policy to an API, a list of policies you can apply appears.

If a policy is already applied, or if the protection it provides is already fulfilled by a policy you applied, the policy appears unavailable. You can filter the list by policy categories:
-
Compliance
-
Security
-
Quality of Service
After selecting a category, you can further filter the list by the kind of protection it fulfills. Any requirements for achieving the level of protection specified by the filter is also listed.
Anypoint Platform provides the following policies:
- Add/Remove Headers
-
Injects or removes HTTP headers from a request or response.
- Client ID Enforcement
-
Enforces the requirement for calls to the API must include a valid client ID and client secret. See footnote.
- Cross-Origin Resource Sharing
-
Allows JavaScript XMLHttpRequest (XHR) calls executed in a web page to interact with resources from non-origin domains. CORS is a commonly implemented solution to the "same-origin policy" that is enforced by all browsers. This policy enables all origins, and makes all resources of an API public.
- HTTP Basic Authentication Policy
-
Enforces authentication per the details configured in a Security Manager policy.
- IP Blacklist
-
Denies API calls from a defined set of IP addresses.
- IP Whitelist
-
Limits API calls to a defined set of IP addresses.
- JSON Threat Protection
-
Protects the target API against malicious JSON that could cause problems.
- LDAP Security Manager
-
Injects an LDAP-based security manager into the target API.
- OAuth 2.0 Access Token Enforcement Using External Provider Policy
-
Configures the API so that its endpoints require a mandatory and valid OAuth 2.0 token. You must reference an external Mule application that serves as the OAuth provider. Update the RAML of your API using the provided snippet before using this policy.
- OpenAM Access Token Enforcement
-
Configures the API so that its endpoints require a mandatory and valid OpenAM token. This policy is only available to organizations using an OpenAM Federated Identity Management system.
- OpenID Connect Access Token Enforcement
-
Configures the API so that its endpoints require a mandatory and valid token. This policy is only available to organizations using an OpenID Connect Management system.
- PingFederate Access Token Enforcement
-
Configures the API so that its endpoints require a mandatory and valid PingFederate token. This policy is only available to organizations using a PingFederate Federated Identity Management system.
- Rate Limiting – SLA-Based
-
Limits the number of messages per time period processed by an API at a maximum value specified in the SLA tier. Any messages beyond the maximum are rejected. Enforcement is based on the client ID passed in the request. See footnote.
- Rate Limiting
-
Limits the number of messages processed by an API per time period at a maximum value specified in the policy. The rate limiting is applied to all API calls, regardless of the source. Any messages beyond the maximum are rejected.
- Simple Security Manager
-
Supports a placeholder security manager that can be configured with a hard-coded username and password for testing purposes.
- Throttling -SLA-Based
-
Throttles he number of messages per time period processed by an API at a maximum value specified in the SLA tier. Any messages beyond the maximum are queued for later processing. Enforcement is based on the client ID passed in the request. See footnote.
- Throttling
-
Throttles the number of messages processed by an API per time period at a maximum value specified in the policy. The throttling is applied to all API calls, regardless of the source. Any messages beyond the maximum are queued for later processing.
- XML Threat Protection
-
Protects the target API against malicious XML that could cause problems.
Note: Update the RAML of your API using the provided snippet before using this policy.