oc create ns <rtf-namespace>Installing Runtime Fabric as a Kubernetes (K8s) Operator
You can install Anypoint Runtime Fabric as a Kubernetes (K8s) operator in the following platforms:
-
Red Hat OpenShift Service on AWS
-
Microsoft Azure Red Hat OpenShift
-
Red Hat OpenShift Dedicated
-
Red Hat OpenShift on IBM Cloud
-
Self-managed Red Hat OpenShift editions (Platform Plus, OCP, Kubernetes engine)
Install Runtime Fabric on Red Hat OpenShift
When you install Runtime Fabric on Red Hat OpenShift, you’ll:
-
Create a Runtime Fabric using Runtime Manager
-
Create a namespace for Runtime Fabric
-
Create a Docker pull secret for pulling the Runtime Fabric component images
-
Optionally, configure shared tenancy
-
Install and configure the Runtime Fabric operator
-
Complete the remaining installation steps to validate your Runtime Fabric and configure ingress
Runtime Fabric also supports OpenShift routes, refer to Configure OpenShift Routes documentation.
Before You Begin
Before installing Runtime Fabric on Red Hat OpenShift, ensure that:
-
You have reviewed the architecture and requirements outlined in Runtime Fabric on Self-Managed Kubernetes
-
You have reviewed the network requirements
-
You have installed and configured a supported Red Hat OpenShift Kubernetes environment with:
-
A supported Kubernetes version
-
An ingress controller to send external requests to applications
-
-
You have privileged user permissions to complete the installation process
-
You have access to the following URLs needed for Red Hat OpenShift registry:
-
registry.connect.redhat.com(See the Red Hat Container Registry Authentication)
-
Create a Runtime Fabric using Runtime Manager
To install Runtime Fabric on Red Hat OpenShift, first create a Runtime Fabric using Runtime Manager. This is required to obtain the activation data which is needed during installation.
-
From Anypoint Platform, select Runtime Manager.
-
Click Runtime Fabrics.
-
Click Create Runtime Fabric.
-
Enter the name of the new Runtime Fabric, then select the Red Hat OpenShift option.
-
Review the Support responsibility disclaimer, then if you agree click Accept.
-
Click Operator.
-
Copy the activation data.
When creating the Runtime Fabric, the business unit you choose is set as the owner business unit. This business unit is referenced in usage reports for reporting allocated cluster capacity. Ensure that you select the correct business unit during installation.
Create A Namespace for Runtime Fabric
In your Kubernetes cluster, create a namespace for installing Runtime Fabric. This namespace is where you install Runtime Fabric components.
To create the namespace, run:
Create A Docker Pull Secret
After you create the namespace, create a pull secret so you can retrieve the Docker images needed to install and run Runtime Fabric.
The default registry URL is rtf-runtime-registry.kprod.msap.io. If you’re using a local registry, specify those values here.
To create the pull secret, run:
oc create secret docker-registry <pull_secret> --namespace rtf --docker-server=<docker_registry_url> --docker-username=<docker_registry_username> --docker-password=<docker_ registry_password>(Optional) Configure Authorized Namespaces
You can optionally configure authorized namespaces, which enable you to deploy Runtime Fabric alongside other services in a Kubernetes cluster.
Before You Begin
Before configuring authorized namespaces, note the following:
-
You must create the
authorized-namespacesConfigMap file before installing Runtime Fabric. Additionally, you must name the ConfigMap,authorized-namespaces. -
The
rtf:resource-metrics-collectorClusterRole has cluster-wide permissions togetandlistnodes, pods, and namespaces and haswatchpermissions for nodes. The role ClusterRole is defined as follows:apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRole metadata: name: rtf:resource-metrics-collector labels: {{- include "labels.standard" . | nindent 4 }} rules: - apiGroups: [""] resources: ["nodes", "pods", "namespaces"] verbs: ["list", "get"] - apiGroups: [""] resources: ["nodes"] verbs: ["watch"]-
In your cluster, create an additional namespace for application deployments, and add the necessary labels to the namespace. To do so, create a YAML file with the following contents:
apiVersion: v1 kind: Namespace metadata: name: <app_namespace> labels: rtf.mulesoft.com/agentNamespace: <rtf_namespace> rtf.mulesoft.com/envId: <environment_id> rtf.mulesoft.com/org: <org_id> rtf.mulesoft.com/role: workers -
Apply the file you just created:
oc apply -f <filename>.yaml -
Repeat steps 1 and 2 to add as many namespaces as you need.
-
Create the RoleBinding for the Runtime Fabric agent ClusterRole that includes the Runtime Fabric agent ServiceAccount. To do so, apply the following configuration in your additional namespace:
kind: RoleBinding apiVersion: rbac.authorization.k8s.io/v1 metadata: name: <name> namespace: <app_namespace> subjects: - kind: ServiceAccount name: rtf-agent namespace: <rtf_namespace> # If using persistence gateway uncomment and provide the following. Ref: https://docs.mulesoft.com/runtime-fabric/latest/persistence-gateway#persistence-gateway-with-authorized-namespaces # subjects: # - kind: ServiceAccount # name: rtf-persistence-gateway # namespace: <rtf_namespace> roleRef: kind: ClusterRole name: rtf:agent-<rtf_namespace> apiGroup: rbac.authorization.k8s.io -
Apply the following RoleBinding template to rtf namespace and any additional namespaces:
apiVersion: rbac.authorization.k8s.io/v1 kind: RoleBinding metadata: name: rtf namespace: <rtf_namespace> roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: system:openshift:scc:anyuid subjects: - kind: ServiceAccount name: rtf-agent namespace: <rtf_namespace> - kind: ServiceAccount name: mule-clusterip-service namespace: <rtf_namespace> - kind: ServiceAccount name: resource-cache namespace: <rtf_namespace> - kind: ServiceAccount name: rtf-persistence-gateway namespace: <rtf_namespace> - kind: ServiceAccount name: cluster-status namespace: <rtf_namespace> - kind: ServiceAccount name: am-log-forwarder namespace: <rtf_namespace> - kind: ServiceAccount name: rtf-certificate-renewal namespace: <rtf_namespace>
-
|
Starting with Runtime Fabric agent version 3.0.0, the |
To use clustered apps in authorized namespaces mode, this RoleBinding must be created:
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
name: rtf-mule-clusterip-service
namespace: <app_namespace>
subjects:
- kind: ServiceAccount
name: mule-clusterip-service
namespace: <rtf_namespace>
roleRef:
kind: ClusterRole
name: rtf:mule-clusterip-service-<rtf-namespace>
apiGroup: rbac.authorization.k8s.ioFor <additional-namespace>, use the same template as well:
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
name: rtf
namespace: <app_namespace>
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: system:openshift:scc:anyuid
subjects:
- kind: ServiceAccount
name: rtf-agent
namespace: <rtf_namespace>
- kind: ServiceAccount
name: mule-clusterip-service
namespace: <rtf_namespace>
- kind: ServiceAccount
name: resource-cache
namespace: <rtf_namespace>
- kind: ServiceAccount
name: rtf-persistence-gateway
namespace: <rtf_namespace>
- kind: ServiceAccount
name: cluster-status
namespace: <rtf_namespace>
- kind: ServiceAccount
name: am-log-forwarder
namespace: <rtf_namespace>
- kind: ServiceAccount
name: rtf-certificate-renewal
namespace: <rtf_namespace>-
Create the
rtf-cluster-version-readerClusterRole and ClusterRoleBinding to allow the Runtime Fabric agent to access OpenShift cluster version information. This is required when using authorized namespaces on OpenShift. Apply this configuration:apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRole metadata: name: rtf-cluster-version-reader rules: - apiGroups: - config.openshift.io resources: - clusterversions verbs: - get - listapiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRoleBinding metadata: name: rtf-cluster-version-reader roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: rtf-cluster-version-reader subjects: - kind: ServiceAccount name: rtf-agent namespace: <rtf_namespace>
-
In your cluster, create a ConfigMap file named
authorized-namespacesand list any additional namespaces. Note that the additional namespace mapping keys must be unique since they use the standard K8s resource (ConfigMap). There is no specific requirements on the format of the key name provided they are unique.apiVersion: v1 kind: ConfigMap metadata: name: authorized-namespaces namespace: <rtf_namespace> data: APPLICATION_NAMESPACE_1: "<app_namespace_1>" APPLICATION_NAMESPACE_2: "<app_namespace_2> -
If, after fully installing Runtime Fabric, you later add or delete any namespaces from the ConfigMap, you must restart the Runtime Fabric agent pod. To do so, run the following command:
oc -nrtf delete po -l app=agentAfter you delete the pod, Kubernetes starts a new one.
Install the Red Hat OpenShift Runtime Fabric Operator
You install the Runtime Fabric operator (rtf-agent-operator) from the OperatorHub.
-
In the Red Hat OpenShift console, navigate to Operators > OperatorHub.
-
In the OperatorHub search field, search for the Runtime Fabric operator.
-
In the rtf-agent-operator dialog, click Install.
| Installing the Runtime Fabric operator requires manual approval and may take several minutes to complete. |
Configure the Runtime Fabric Operator
To configure the Runtime Fabric operator, you supply the necessary values when prompted.
-
In the Red Hat OpenShift console, navigate to Operators > Installed Operators.
-
In the console, switch the value of Project to the namespace you created for installing Runtime Fabric.
-
In the console, click Create Instance, and select Configure via form view.
Do not change the name of the instance. Doing so can create installation errors.
-
Add any required parameters. Refer to the Installation Parameters Reference for guidance.
If you’re using authorized namespaces, set
authorizedNamespacestotrue. -
Click Create.
Installation Parameters Reference
The following is an example YAML view of the installation parameters.
activationData: <activation_data>
proxy:
http_proxy:
http_no_proxy:
monitoring_proxy:
custom_log4j_enabled: true
muleLicense: <mule_license_key>
global:
authorizedNamespaces: false
image:
rtfRegistry: <rtf-runtime-registry.kprod.msap.io or local registry value>
pullSecretName: rtf-pull-secret
containerLogPaths:
- /var/lib/docker/containers
- /var/log/containers
- /var/log/podsRequired Parameters
The values for these required parameters are set when you create the Runtime Fabric in Runtime Manager. If you’re not using a local registry, use the default values for the registry URL and pull secret.
| Key | Value | Example |
|---|---|---|
|
Activation data |
YW55cG9pbnQubXVsZXNvZnQuY29tOjBmODdmYzYzLTM3MWUtNDU2Yy1iODg5LTU5NTkyNjYyZjUxZQ== |
|
Registry URL |
|
|
Registry secret |
|
|
Mule license for applications |
|
Optional Parameters
Set these optional parameters as needed.
| Key | Value | Example |
|---|---|---|
|
Enables or disables custom Log4j configurations |
|
|
Enables or disables additional namespaces |
|
|
Enable authorized namespaces |
|
|
Proxy and no_proxy values |
|
|
Anypoint Monitoring proxy values |
|
|
The Filebeat read path |
|
Insert the Mule License Key
If you didn’t add the Mule license key during install, you can add it using the rtfctl command line utility or Helm.
Before you install the license key, encode it to Base64 format.
Encode the License Key
-
On MacOS, run the following command:
base64 -b 0 -i <license-file> -
On Unix, run the following command:
base64 -w0 <license-file> -
On Windows, choose one of the following:
-
Use a WSL or Cygwin shell that includes the base64 tool and use the above Unix command.
-
Use the base64.exe program included with Windows git (C:\Program Files\Git\usr\bin).
-
Use the following Powershell command:
$BASE64_ENCODED_LICENSE=[convert]::ToBase64String((Get-Content -path "license.lic" -Encoding byte))
-
Apply the License Key from the OpenShift Console
To apply the license key from the OpenShift console, follow these steps:
-
Navigate to the Runtime Fabric operator.
-
Select the namespace in which the Runtime Fabric instance is installed.
-
Click on the Runtime Fabric tab.
-
Click on the runtime-fabric instance link.
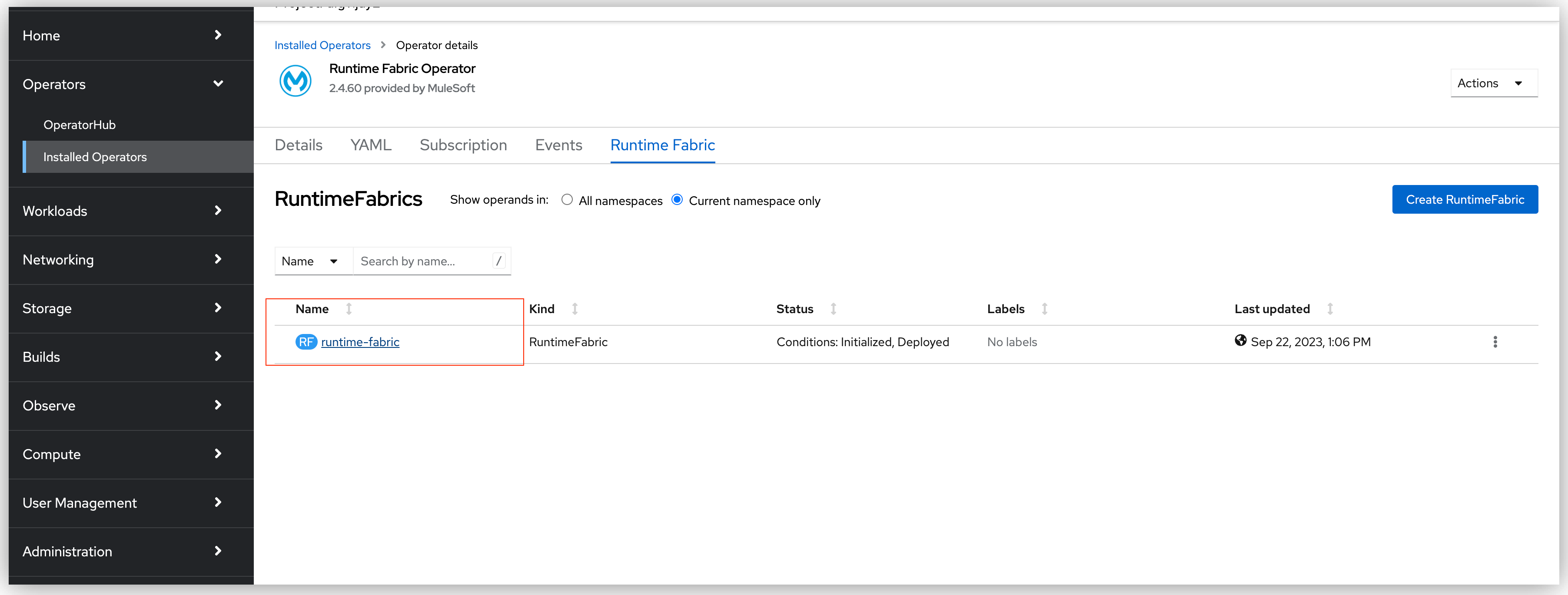
-
Update the Runtime Fabric instance CR .yaml file by adding the
muleLicense.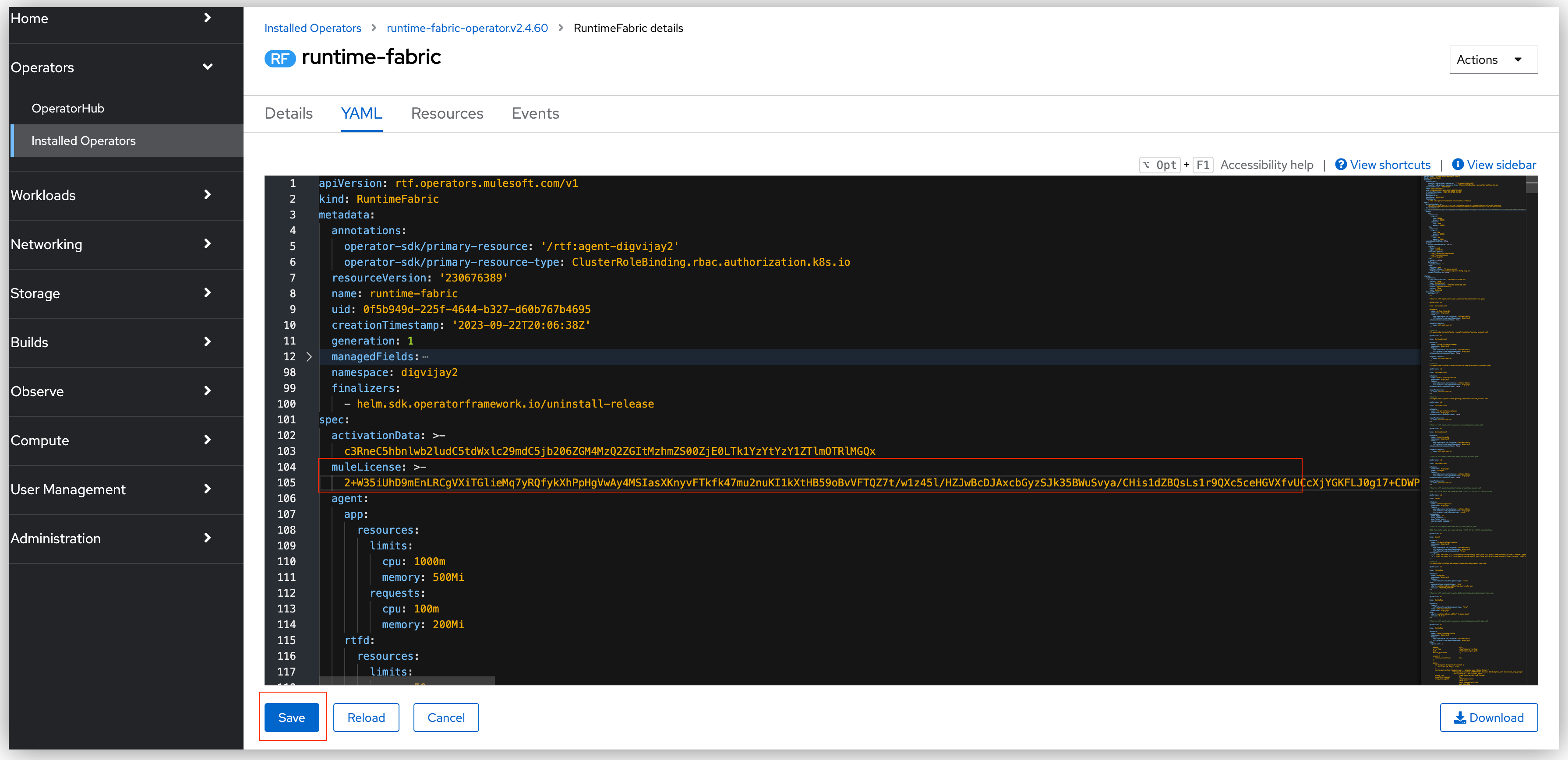
Configure the Ingress Resource Template
If your ingress controller requires custom annotations and ingress class definition, follow the instructions in Defining a Custom Ingress Configuration.
|
For GKE customers, the ingress controller included with GKE will provision a separate HTTP load balancer per application by default. Please read this KB article for more details. |
Validate Your Runtime Fabric
After completing the installation, your Runtime Fabric should be activated within your Anypoint organization. To validate your installation, go to Anypoint Runtime Manager and confirm that the status of the Runtime Fabric is Active.
Before deploying an application to your Runtime Fabric:
-
Associate the Runtime Fabric with at least one Anypoint environment.
-
Review and update the Inbound Traffic settings based upon your Kubernetes environment.
-
Deploy an application to verify that Runtime Fabric is installed and configured correctly.
Prepare for Deploying Mule Apps to Red Hat OpenShift
Before you deploy any Mule applications to your Red Hat OpenShift cluster, ensure that you’ve installed your Mule license key and then, perform the following steps.
Also, before attempting to deploy an Mule applications, ensure that you’ve installed your Mule license key.
-
Create a namespace for your Mule app deployments. See Creating Application Namespaces for Application Deployments.
-
From Runtime Manager, deploy a Mule app using your namespace. See Deploy Mule Applications to Runtime Fabric for instructions.



