Enable DoS for a WAF Policy
You can configure actions in an existing DoS policy to apply to WAF errors, for example, blocking an IP address for a specified time interval. In a WAF policy, WAF errors are rejected and a status code of 400 is returned, however WAF processing is expensive, so you may want to add WAF errors to a DoS policy to protect resource usage.
If you don’t configure your DoS policy (apply DoS thresholding) for WAF errors, parsing request bodies can consume a large share of CPU. If you receive many requests, just detecting errors will consume a large share of CPU. If DoS thresholding is implemented, when the threshold for DoS is exceeded, it ceases to parse request bodies.
When a blocked IP address attempts to connect, the request will be rejected based solely on the IP address. This is extremely efficient. If Drop Silently is enabled for DoS, the TLS connection isn’t attempted, which saves more resources.
IP addresses coming from a malicious source may be attempting many other requests other than those triggering WAF. Some of these requests may look valid. When the DoS threshold is exceeded, all requests, good or bad, are dropped for the identified IP address.
Escalate a WAF Policy to DoS
To escalate a WAF policy to DoS, verify that the Denial of Service Policy exists.
-
In Security Policies, select the DoS policy in the list and click Edit.
-
In the left menu, click WAF Errors.
-
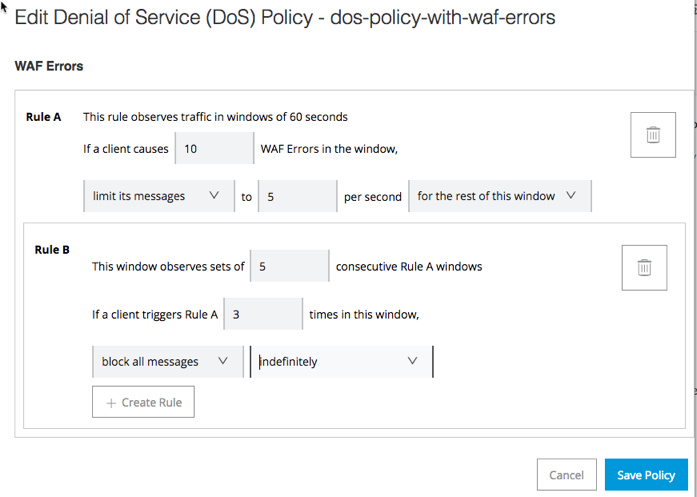
Configure the WAF errors, and click Save Policy.
All WAF errors will be handled by the thresholds you configure in the DoS policy.
In this example, for Rule A, all requests for the source IP address are limited if more than 10 WAF errors are received within a 60-second time interval. (The default is 60 seconds, but you can change this value in the General tab for the DoS policy.)
In Rule B, the settings shown will block an IP address indefinitely if it causes the specified WAF error three times in a period of five Rule A intervals (5 60-second intervals in this case).
For more information about configuring DoS policies, see Denial of Service Policy



