Anypoint Security Policies for Edge
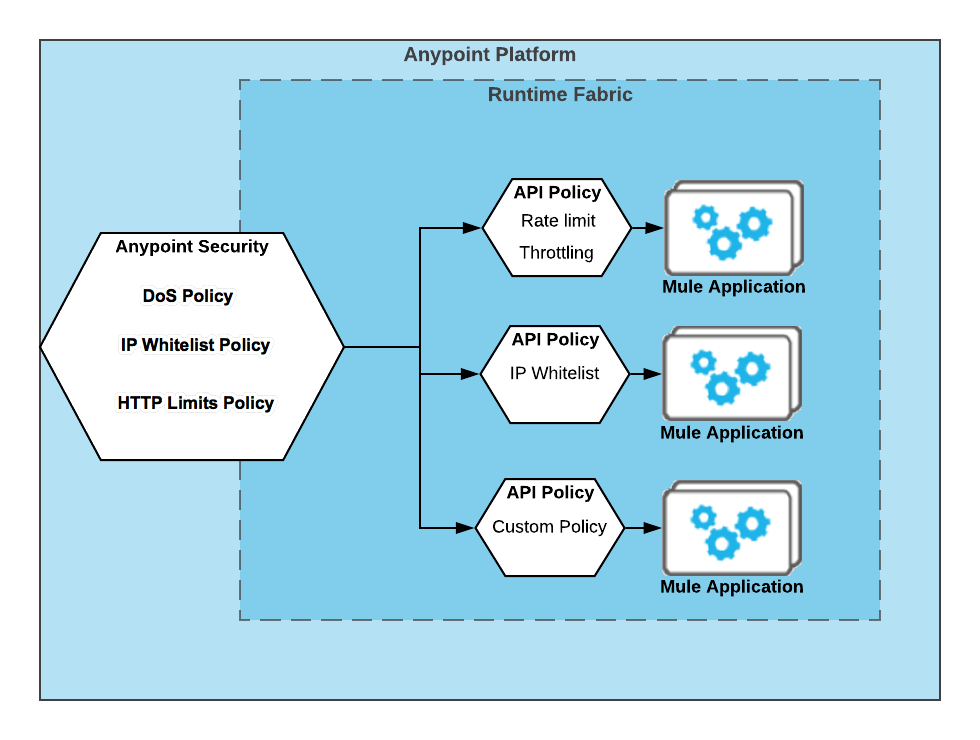
Anypoint Security features a high-performance, reliable, and scalable service that works with Anypoint Runtime Fabric to enforce security policies on nodes deployed to your Anypoint Runtime Fabric. Anypoint Security provides denial-of-service (DoS), IP allowlists, HTTP limits, and Web Application Firewall (WAF) policies to protect your APIs.
You can use the Anypoint Security policies to manage all traffic to your Runtime Fabric, and leverage API Manager policies to apply specific behaviors to specific APIs.

Anypoint Security policies then act as a default router capability through which all traffic traverses.
-
Threat detection and prevention
-
Content attack prevention (HTTP header and message limits checks)
-
Denial of Service
-
IP allowlists
-
-
Advanced TLS (for example, certificate pinning, CRL)
-
Basic TLS (for example, Mutual TLS, SSL Termination)
API policies that are configured in API Manager and running through an API gateway give you the ability to further customize or extend certain limitations you are applying at the Mule application level.
This layer of security provides the same control as any API Manager policy offers. For example:
-
Basic TLS (for example, mutual TLS, SSL termination)
-
Rate limiting
-
OAuth
-
Authorization and Accounting (AAA)
Prerequisites
| Anypoint Security Edge is not supported for Runtime Fabric on self-managed Kubernetes deployments. |
To configure and use the security policies, you must:
-
Have the Anypoint Security - Edge entitlement for your Anypoint Platform account.
If you don’t see Security in Management Center, contact your customer success manager to enable Anypoint Security for your account.
-
Have Runtime Fabric on VMs/Bare Metal with inbound traffic configured. Anypoint Runtime Fabric is a container service that automates the deployment and orchestration of Mule apps and API gateways.
Refer to the Runtime Fabric documentation.
Runtime Fabric requires the Anypoint Integration Advanced package or a Platinum or Titanium subscription to Anypoint Platform.
-
Enable inbound traffic on Runtime Fabric to allow Mule apps and API gateways to listen on inbound connections.
DoS Policy
DoS policies are designed to protect your network nodes against malicious clients trying to flood your network to prevent legitimate traffic to your APIs.
Learn more about the DoS policy.
IP Allowlist Policy
Create an IP address allowlist policy to configure an explicit list of IP addresses that can access your deployed endpoints.
Learn more about the IP Allowlist.
HTTP Limits Policy
HTTP limits policies prevent attacks from clients that send large messages that can consume all of your processing bandwidth.
Learn more about the HTTP Limits policy.
WAF Policy
WAF policies provide the Open Web Application Security Project (OWASP) Core Rule Set (CRS) for checking requests and responses to detect common web application attacks.
Learn more about the WAF policy.



