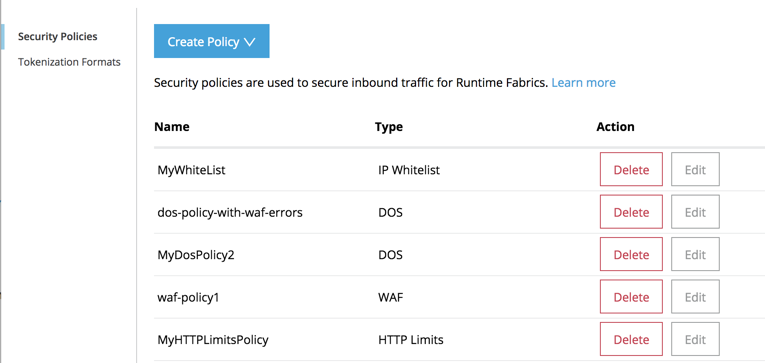
Create a Web Application Firewall Policy
You can create a Web Application (WAF) policy in Anypoint Security > Security Policies to implement firewall security policy enforcement between your web application and client endpoint. WAF violation detection policies can also be escalated to Denial of Service (DoS) so that IPs and connections can be blocked.
Prerequisites
To configure and use the security policies, you must:
-
Have the Anypoint Security - Edge entitlement for your Anypoint Platform account.
If you don’t see Security in Management Center, contact your customer success manager to enable Anypoint Security for your account.
-
Have Runtime Fabric on VMs/Bare Metal with inbound traffic configured. Anypoint Runtime Fabric is a container service that automates the deployment and orchestration of Mule apps and API gateways.
Refer to the Runtime Fabric documentation.
Runtime Fabric requires the Anypoint Integration Advanced package or a Platinum or Titanium subscription to Anypoint Platform.
-
Enable inbound traffic on Runtime Fabric to allow Mule apps and API gateways to listen on inbound connections.
Create the Policy
-
Sign into Anypoint Platform and navigate to Anypoint Security.
-
In the Security Policies page, click Create Policy and select Web Application Firewall (WAF).
-
Enter a Name for the policy and click Save Policy.
The policy appears in the Security Policies list, where you can edit and delete policies.

Configure Request Rulesets
Configure the rules to allow or block request traffic to your web application. For more information about request rulesets, see Request rulesets.
-
In the menu on the left, click Request Rulesets.
All the rules are disabled by default. For each rule, you can:-
Disable ruleset - (Default) Ruleset detection is turned off.
-
Detect and allow violations - The violation is detected and you will get information, per incident, in your log at the
INFOlevel. -
Detect and reject violations - The request is rejected and returns a response status of
HTTP/1.1 400 BAD REQUEST - web application firewall, and DoS is notified that a rule was triggered. If DoS has been configured for WAF Errors, DoS updates its WAF-related counters and takes action, if necessary. If DoS isn’t configured for WAF Errors, it ignores the notification it receives from WAF.
Information about the violation is also sent to the log, per incident, atINFOlevel.When you hover over the
ito the right of each rule, the rule ID range for that ruleset is displayed. You can use this information for testing rulesets.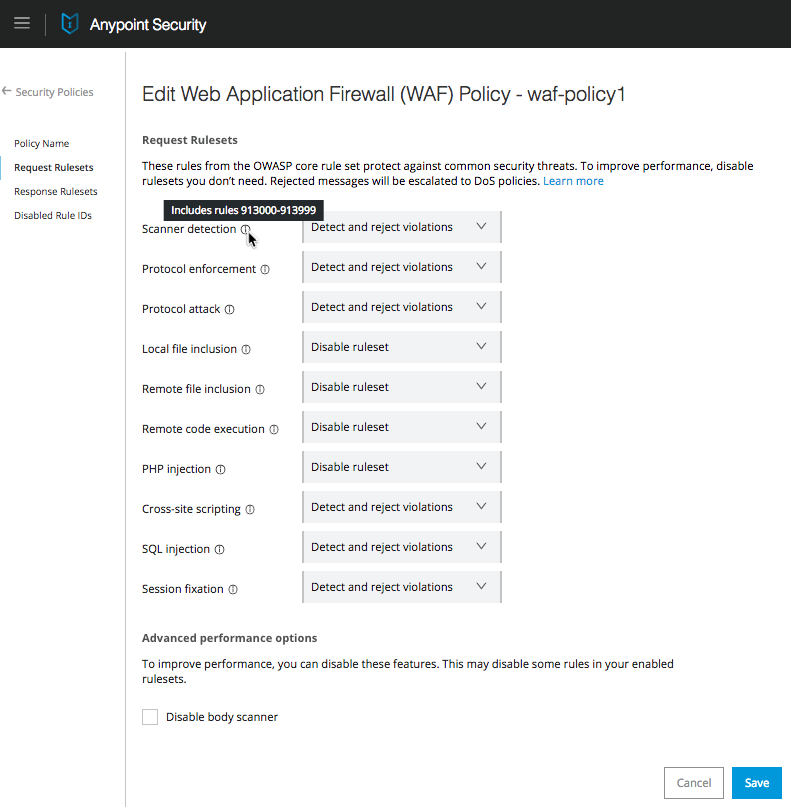
-
-
In Advanced performance options, select one of the following options:
-
Disable body scanner. By default, the request body is scanned unless the body is larger than 1 MB, in which case the scan is skipped.
Check this option if request body scanning isn’t needed, or to reduce CPU consumption.If a body is larger than 1 MB, the scan is skipped, even if you do not select Disable body scanner. -
Detect sensitive information - If you select this option, the request body is scanned for sensitive information, and when you apply the WAF policy to Runtime Fabric, the log summary (
rtfWafSecurityPolicySummary) records the count and number (rule ID) of the sensitive information pattern that is detected.This option is not allowed if Disable Body Scanner is selected. An rtfSidSummarylog is also generated, which contains the API, rule, direction, and count for instances of sensitive information.
-
-
Click Save Policy.
Configure Response Rulesets
Configure the rules to allow or block responses to your web application. For more information about response rulesets, see Response rulesets
-
In the menu on the left, click Response Rulesets.
All the rulesets are disabled by default. For each rule, you can:-
Disable ruleset - (Default) Ruleset detection is turned off.
-
Detect and allow violations - The violation is detected and you will get information, per incident, in your log at the
INFOlevel. -
Detect and reject violations - The request is rejected and returns a response status of
HTTP/1.1 400 BAD REQUEST - web application firewalland information about the violation is also sent to the log at INFO level per incident.
-
-
In Advanced Performance Options, select one of the following options:
-
Disable body scanner - By default, the response body is scanned unless the body is larger than 1 MB, in which case the scan is skipped.
Check this option if response body scanning isn’t needed, or to reduce CPU consumption.
This option works the same as it does for the request ruleset with some additional important caveats: -
Response messages must have one of the following MIME types in the content type header, or the WAF rules will not be evaluated:
-
text/plain
-
text/html
-
text/xml
-
application/json
-
-
Detect sensitive information - If you select this option, the response body is scanned for sensitive information, and when you apply the WAF policy to Runtime Fabric, the log summary (
rtfWafSecurityPolicySummary) records the count and number (rule ID) of the sensitive information pattern that is detected.This option is not allowed if Disable Body Scanner is selected. An rtfSidSummarylog is also generated, which contains the API, rule, direction, and count for instances of sensitive information.
-
-
Click Save Policy.
Disable Individual Rules
If individual rules cause false positives, you can disable them. This is useful because if only one rule in the ruleset is causing a false positive, it isn’t necessary to turn off an entire ruleset such as “Protocol attack."
You can examine the WAF summary message in logs to determine which rule IDs are firing. You can also check the Anypoint Security policy’s RAML for a complete list of rule IDs.
-
In the Anypoint Security > Security Policies page, click Edit for the WAF policy to disable rules.
-
In the menu on the left, click Disabled Rule IDs.
-
Add the individual rule IDs for the rules to disable, separated by commas.
-
Click Save Policy.
Once your WAF policy is configured and saved, you can (optionally) edit an existing DoS policy to enable DoS for your WAF policy, then deploy the policies to Runtime Fabric.



