Enabling Single Sign-On for Your Portal
Administrators or security teams can implement an external identity provider (IdP) as a login option for an API Experience Hub portal. Single sign-on (SSO) authentication provides a seamless login experience for your customers with your organization’s unique branding. Your users can log in to your portal without having to remember another username and password or entering login credentials multiple times.
After a member of your portal visits the portal page and selects the SSO option, they’re redirected to the identity provider login page to authenticate. The SSO authentication process uses the identity provider to check the identity of a user. If the login is successful, the user that aligns with the user profile is created in Access Management. The API Experience Hub portal home page appears for the user to browse and discover APIs.
API Experience Hub supports multiple IdPs for SSO.
Access Management configures identity management for SSO for Anypoint Platform. For more information about identity providers, see Identity Management in Access Management.
Configuring SSO
The high-level steps for setting up SSO for your portal vary depending on your use case.
-
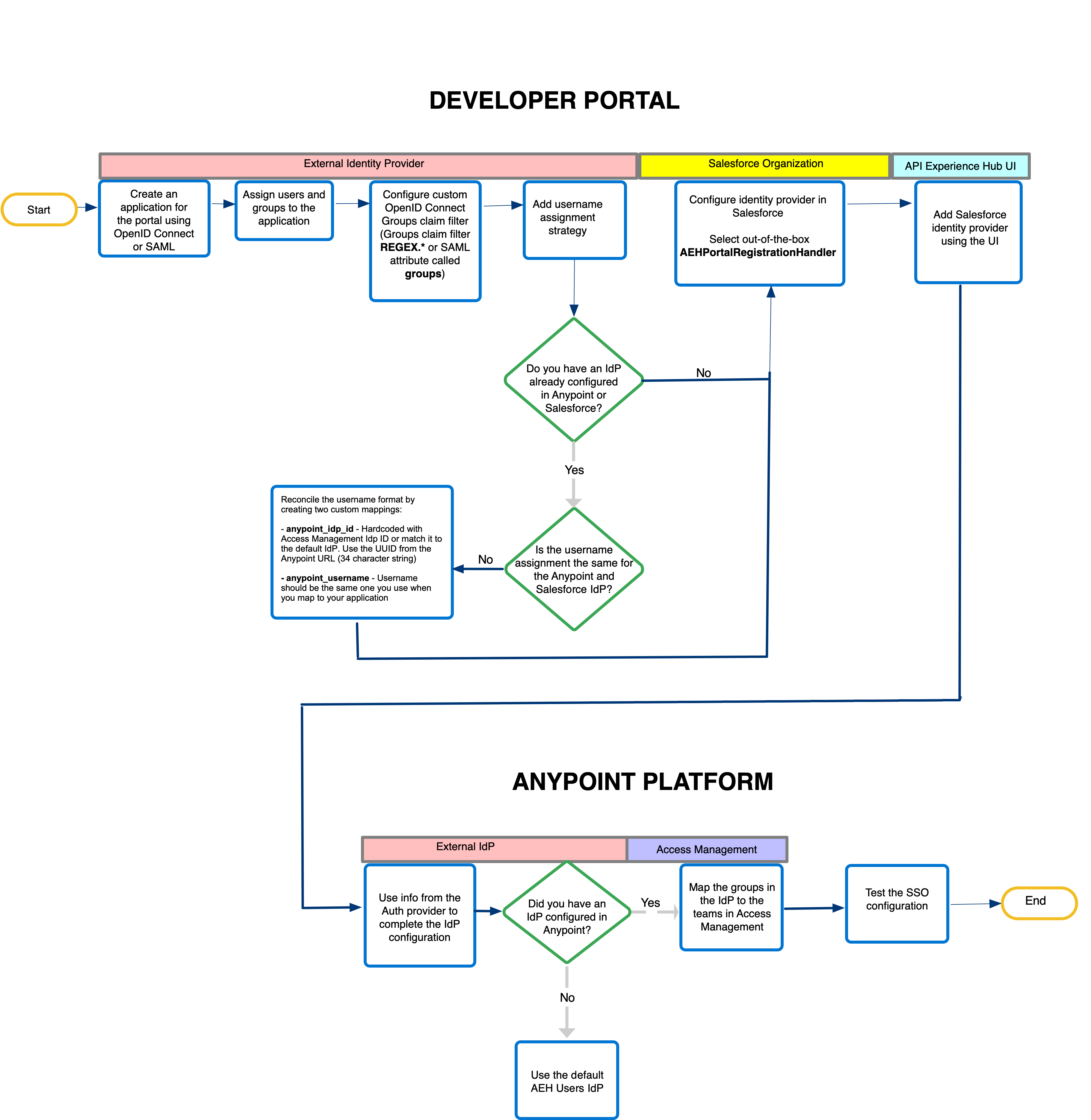
Step 1: Enable SSO for Your Portal
In this step, you create and configure an application in the identity provider.
You can configure an identity provider for Anypoint Platform and Salesforce can be configured using OpenID Connect or SAML (Single Sign-on Settings). Microsoft Azure OpenID Connect isn’t supported.
-
Step 2: Add Salesforce Identity Providers
In this step, you add and enable the Salesforce identity provider from API Experience Hub UI. Once the identity provider is enabled, users can see the login option from the portal’s login page.
-
In this step, you map the groups created in the Salesforce identity provider that you added to the corresponding team profile for the portal.
-
Step 4: Test the SSO Configuration
In this step, you test the SSO configuration that you just set up for the portal.
This diagram shows the overall steps to take in the external identity provider, Anypoint Platform, and Salesforce to set up your single sign-on configuration:

Out-of-the-Box Configurations
API Experience Hub provides the following out-of-the-box configurations to assist the process of enabling SSO:
-
anypoint_idp_id
The custom claim or SAML attribute provides the information that’s received from the identity provider that determines which Anypoint Platform identity provider to map a user to.
-
AEH Users - ${salesforceOrganizationId}
The default Anypoint Experience Hub identity provider that’s created in Anypoint Platform to map all self-registered users. This identity provider is used when the aeh_portal_idp isn’t set in the identity provider. Self-registered users are mapped with the default identity provider.
-
AEH Portal - ${salesforceOrganizationId}_$*{salesforceCommunityId}
This solution creates a team called AEH Portal in Access Management automatically. This team includes administrators, guests, and members profiles. You select this team when adding the group mapping.
-
AEHPortalRegistrationHandler.cls
A single Apex class is provided in the API Experience Hub package called AEHPortalRegistrationHandler.cls that is compatible with SAML and OpenID Connect.
The registration handler is Apex code that runs when a user logs in to the Salesforce Experience Cloud site. You select this handler when configuring an authentication provider for Salesforce. When the identity provider is configured properly, Salesforce passes the portal ID to the AEHPortalRegistrationHandler. If the user does not exist, the registration handler creates the user’s identity in Salesforce. If the user exists, the handler updates the user metadata based on information sent by the identity provider, for example, the user’s first name and last name. The registration handler uses the portal ID in Salesforce to load specific configurations by the portal. For example, the registration handler creates the user in the profile and account related to the portal from the NetworkSelfRegistration object.
Basic Terminology
The following terms are referenced in this topic:
- Authentication Provider
-
An authentication provider is a framework that allows you to connect Salesforce to a third party for authorized data access, authentication, or both, depending on the protocol. Authentication providers can implement OAuth 2.0 to authorize Salesforce to access third-party data. Or they can implement OpenID Connect or custom authentication protocols to support both third-party data access and authentication.
When you’re using authentication providers, Salesforce is always the relying party. If the authentication provider implements OpenID Connect, we refer to the third party as the OpenID provider. If it implements a custom authentication protocol, we call the third party the identity provider.
- Identity Provider
-
An identity provider acts as a trusted service that authenticates a user’s identity.
- OpenID Connect
-
OpenID Connect is an open standard authentication protocol built on OAuth 2.0. With OpenID Connect, the relying party and OpenID provider can exchange information about who a user is and what they can do with a service.
- OpenID Provider
-
In OpenID Connect, an identity provider is called an OpenID provider. It authenticates users as requested by the relying party.
- Relying Party
-
In OpenID Connect and custom authentication protocols, a service provider is called a relying party, though some use the terms interchangeably. It relies on the OpenID provider or identity provider for authentication.
- Security Assertion Markup Language (SAML)
-
SAML is an open standard authentication protocol that you can use to implement SSO in your Salesforce org. SAML allows identity providers and service providers to securely exchange user information, enabling user authentication between services.
- Single Sign-On
-
Single sign-on (SSO) is an authentication method that enables users to access multiple applications with one login and one set of credentials. For example, after users log in to your org, they can automatically access all apps from the App Launcher. You can set up your Salesforce or Anypoint Platform organization to trust a third-party identity provider to authenticate users. Or you can configure a third-party app to rely on your org for authentication.



