Discovering and Cataloging External Agents with Scanners
Use agent scanners to automatically discover and catalog agents from outside Anypoint Platform. Scanners inspect agent ecosystems on diverse platforms to provide enterprise-grade governance and visibility through MuleSoft Agent Fabric. They extract metadata from agents and tools and synchronize the information with the Agent Fabric registry in Anypoint Exchange.
Create a scanner to connect to external provider platforms and transform native metadata into the canonical Agent-to-Agent (A2A) format. The system detects updates and resolves conflicts to maintain a single source of truth. This secure, metadata-first integration operates as a read-only mechanism to avoid complexity and permission challenges in external systems.
Add and configure a scanner to discover and catalog agents. Schedule scans to run at specific intervals and configure the connection and email notifications. After a scan is complete, view a summary of added agents and the scan history.
Scanners add supported agents to Agents & Tools as agent asset types. They detect new and missing agents and identify metadata updates. Subsequent scans overwrite metadata changes and restore agents deleted from Exchange. To retain changes, update the asset in the agent provider‘s source.
After you add a scanner to a business group, you can’t move the scanner or its assets to another group. View a list of scanners on the Agent Scanners page. The list displays information about the scanner status, name, agent provider, the last run status, the next run, and the added agents.
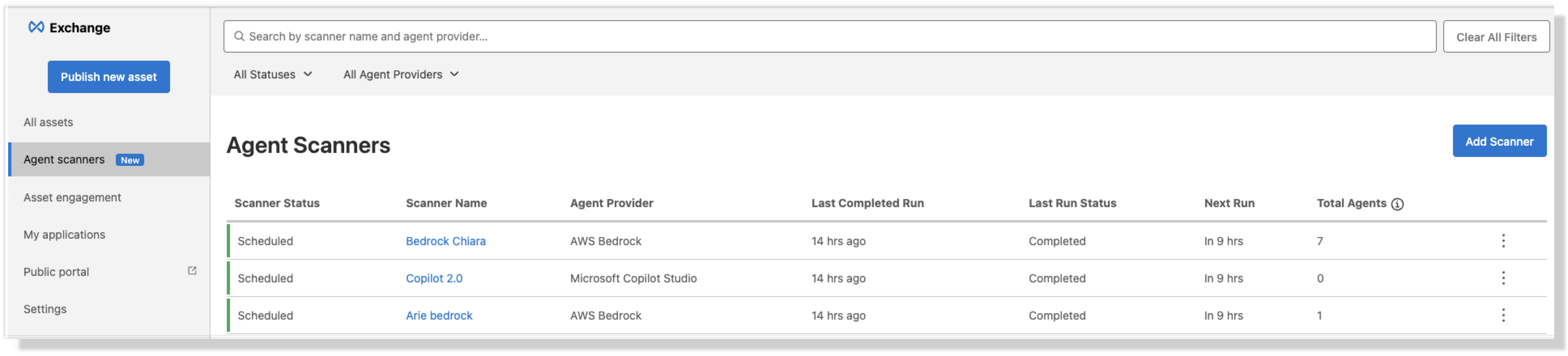
Agent scanners support these providers:
-
Amazon Bedrock
-
GoDaddy ANS
-
Google Vertex AI
-
Microsoft Copilot Studio
Security and Data Retention
Agent scanners register agent assets as read-only because the data originated from the agent provider’s platform. Sensitive information, such as API keys and tokens, are securely stored in Anypoint Security secrets manager. To maintain compliance, create credentials with limited permissions. Scanners don’t write data to your source system, but read-only access ensures the highest security.
The system retains scan logs and statuses for at least 90 days and never deletes the most recent successful run.
Scanners enforce these limits:
-
Frequency: Once daily
-
Retrieval: 1,200 agents per runtime limit
-
Runtime: 6 hours
If a scan exceeds the runtime limit, the scanner saves the progress and continues the scan the next time it runs.



