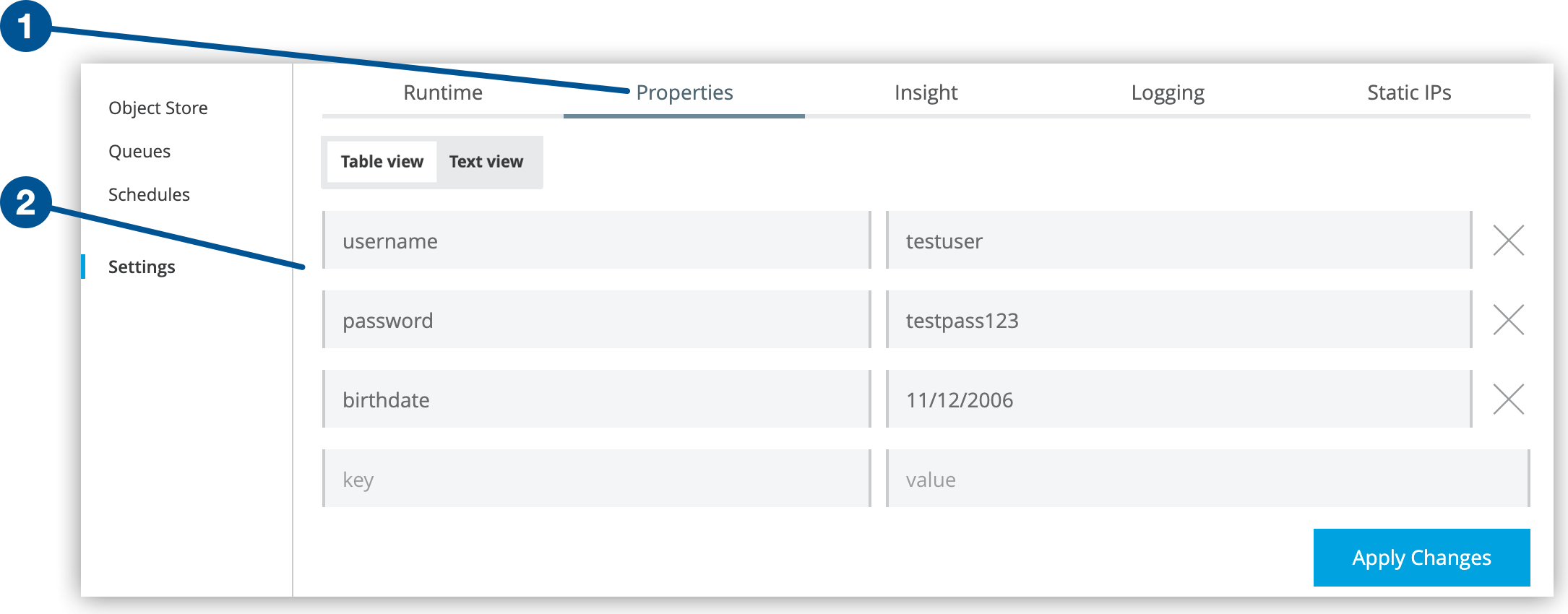
Encrypted properties that are bundled with a Mule application inside a secure properties placeholder file do not appear in the Runtime Manager Properties tab. This keeps the values safely locked inside the Mule application.
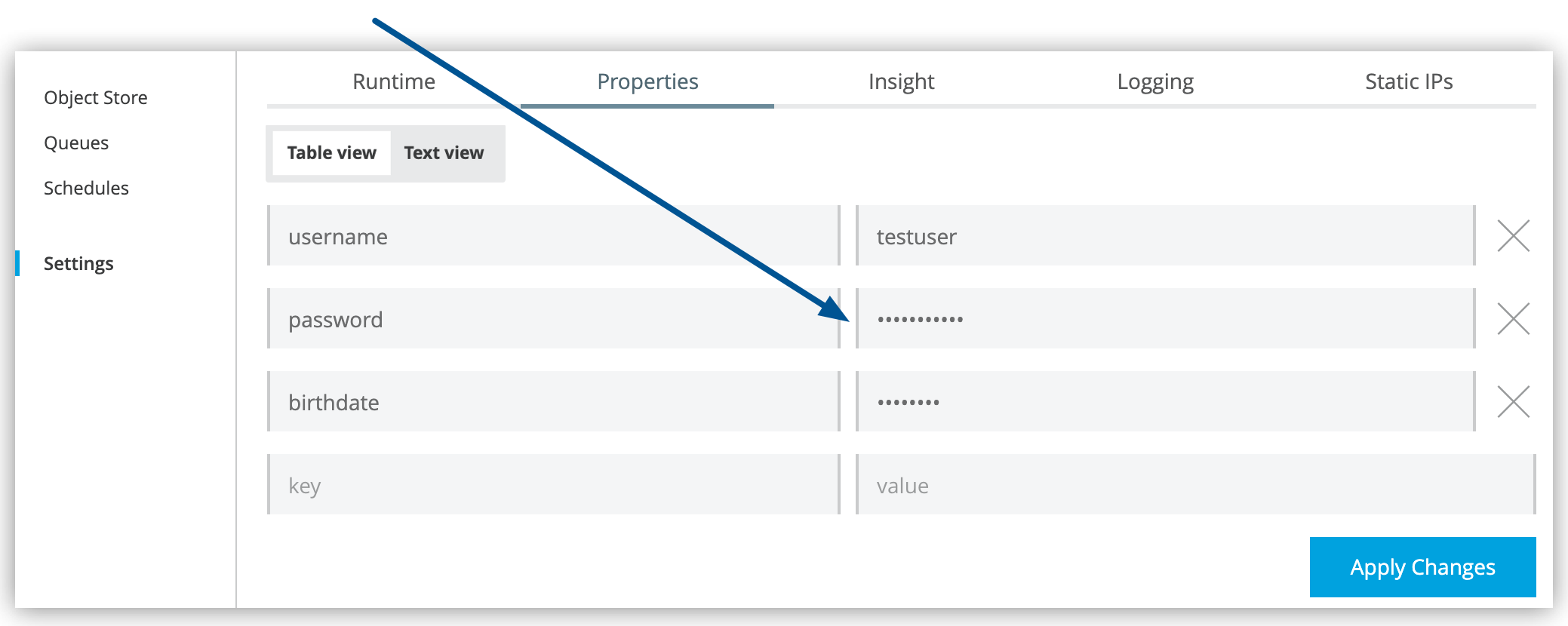
If encrypted property names are listed in the Mule application’s secureProperties entry in mule-artifact.json, once the application is deployed, the value of the encrypted property names is hidden in the Runtime Manager Properties tab, along with decrypted properties.
The decrypted values are stored securely in the Mule worker’s memory and the encrypted values are stored in the CloudHub database for your user account. The decrypted values are never stored in any CloudHub worker’s files, nor are they ever passed between any other machines (including the Runtime Manager console).
So for any encrypted property that is also marked as hidden in the Mule application’s secureProperties entry, you can safely replace any encrypted property with a clear-text value. The clear-text value is then securely stored in the CloudHub properties database, and securely passed into the Mule application every time the Mule application is started.
For CloudHub deployments, the new value is hidden once the application is deployed and can never be viewed again.
For hybrid deployments, the new value remains visible, even after the redeployment.
This means that when you override a secure property in the CloudHub Properties tab for the application, the value must not be encrypted. In this scenario, only users who have access to the values in the application’s source files when they deploy or redeploy a secure application can override secure properties.
An example of when to override secure properties is if you need to update the database user and password stored in two properties named db.user and db.password in a production application. You can enter the new db.user and db.password values in the CloudHub Properties tab for the application and then start or restart the application. This allows the new application to upgrade the secure login information with zero downtime.
After all dependent applications are migrated, the old account can be decommissioned.
|
|
If you use the Table View in the application’s Properties tab to update properties, you don’t need to escape the colons in property names, for example: secure::someproperty. If you use the Text View to update properties, you need to escape the colons in property names, for example: secure\:\:someproperty.
|