String
Amazon Secrets Manager Properties Provider Examples
The following examples enable you how to configure Amazon Secrets Manager Properties Provider to retrieve your secrets from Amazon Secrets Manager cloud service
|
When using dynamic configurations (such as |
Configure AWS Connection Types
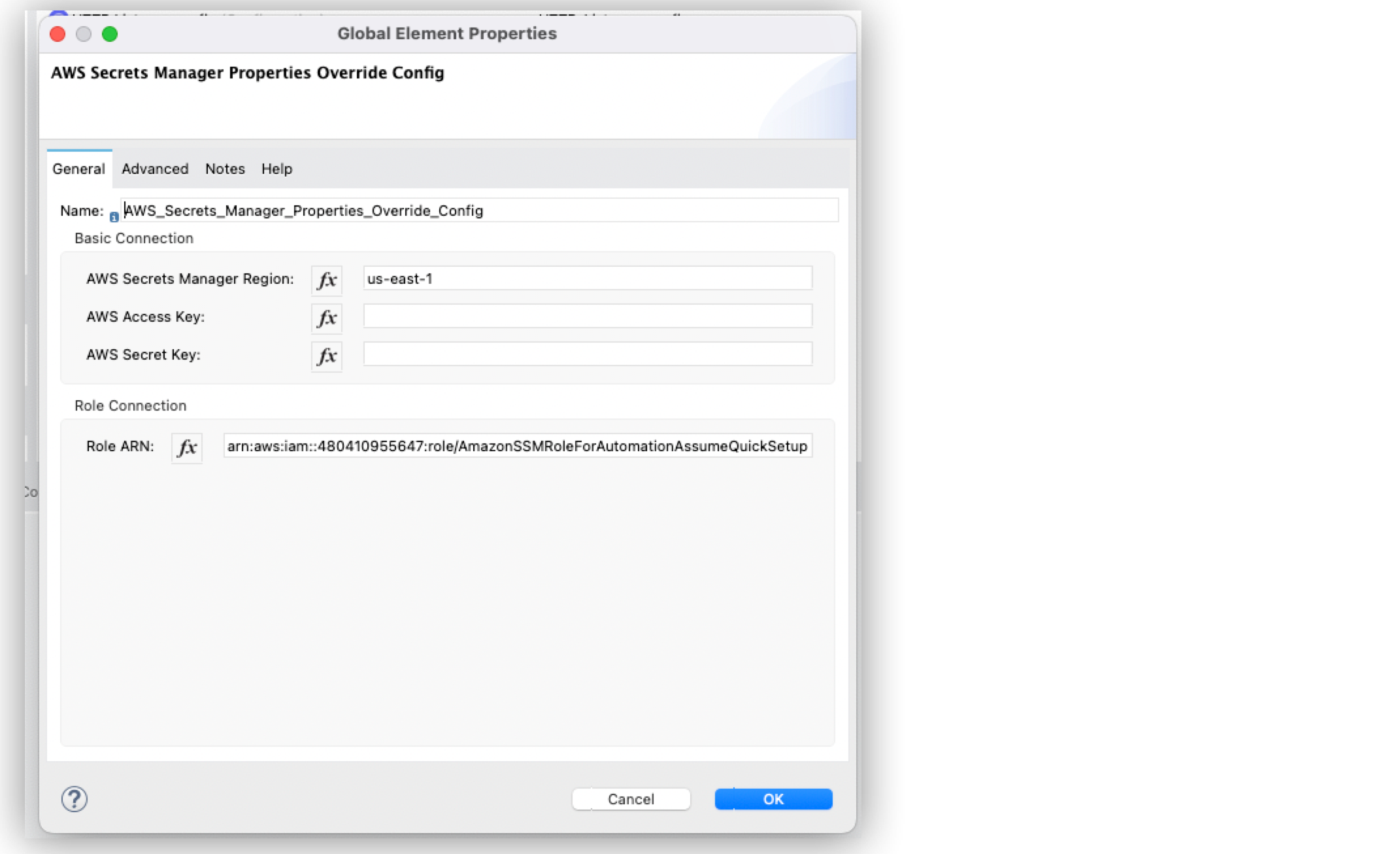
Anypoint Connectors can use Amazon Secrets Manager Properties Provider in their configurations. The following example illustrates how to configure the AWS connection type in the AWS Secrets Manager Properties Override Config of Anypoint Studio:
-
In Studio, navigate to the Global Elements tab.
-
Click Create.
-
In the Choose Global Type window, type
AWS Secrets Manager. -
Select AWS Secrets Manager Properties Override Config.
-
Click OK.
-
In the Global Element Properties window, you can configure the following fields:
| Name | Type | Description | Default Value | Required |
|---|---|---|---|---|
AWS Secrets Manager Region |
AWS Secrets Manager region, for example, |
x |
||
AWS Access Key |
String |
AWS access key ID. |
||
AWS Secret Key a |
String |
AWS secret key ID. |
||
Role ARN |
String |
Uniquely identifies a role to gain cross-account access. |
||
External ID |
String |
The External ID is used to prevent the confused deputy problem when assuming a role in another account. |
In the Configuration XML editor, the configuration looks like this:
<aws-secrets-manager-properties-override:config name="AWS_Secrets_Manager_Properties_Override_Config" doc:name="AWS Secrets Manager Properties Override Config" doc:id="4507e2b4-3205-4400-b903-848dcba504a7" >
<aws-secrets-manager-properties-override:basic-connection region="us-east-1" />
<aws-secrets-manager-properties-override:role-connection roleARN="arn:aws:iam::480410955647:role/AmazonSSMRoleForAutomationAssumeQuickSetup" externalId="38cf7bd2-decf-4ac3-8cff-cbad32f29bg9" />
</aws-secrets-manager-properties-override:config>If you do not provide credentials, the default AWS connection follows the default credentials provider chain - AWS SDK for Java 2.x.
Configure AWS Secrets Manager Using a JSON String
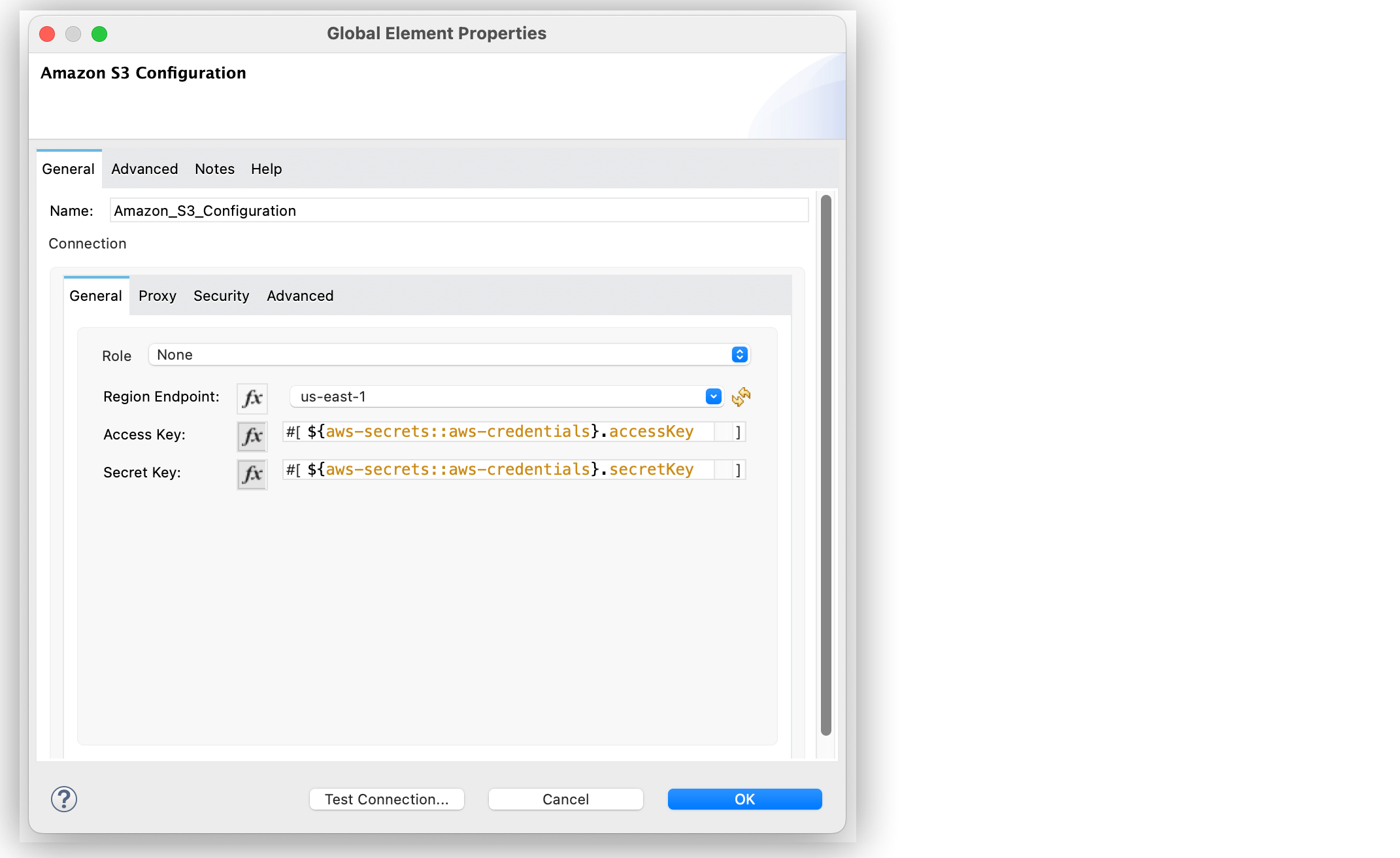
The following example shows how to configure the Amazon Secrets Manager Properties Provider for Amazon S3 Connector by using a JSON string where you create the secret manager keys.
Based on a JSON file that contains accessKey and secretKey:
aws secretsmanager create-secret --name aws-credentials --secret-string '{"accessKey":"ACCESSKEY", "secretKey":"SECRET"}'
-
In the Amazon S3 Configuration global element properties window, select fx to set expression values.
-
Set Access Key to
${aws-secrets::aws-credentials}.accessKey. -
Set Secret Key to
${aws-secrets::aws-credentials}.secretKey.
In the Configuration XML editor, the configuration looks like this:
<s3:config name="Amazon_S3_Configuration" doc:name="Amazon S3 Configuration">
<s3:connection accessKey="#[${aws-secrets::aws-credentials}.accessKey]" secretKey="#[${aws-secrets::aws-credentials}.secretKey]" />
</s3:config>Handle JSON Keys with Dots
If your JSON secret contains keys with dots in their names, DataWeave treats the dots as subtrees in JSON. Make sure that configuration fields are set to Expression mode (fx button enabled) when using these syntaxes.
For example, with this JSON structure, access the value using ${aws-secrets::mySecretName}.'myProject.demo.accessKey'.
{
"myProject.demo.accessKey": "XXXXXXXX",
"myProject.demo.secretKey": "XXXXXXXX",
"myProject.demo.region": "us-east-1",
"myProject.demo.roleArn": "arn:aws:iam::XXXXXXXXXXX:role/AmazonDemoTestRole",
"myProject.example.http.Port": "8081"
}
For example, with this JSON structure, access the value using ${aws-secrets::mySecretName}.myProject.demo.accessKey.
{
"myProject": {
"demo": {
"accessKey": "XXXXXXXX",
"secretKey": "XXXXXXXX",
"region": "us-east-1",
"roleArn": "arn:aws:iam::XXXXXXXXXXX:role/AmazonDemoTestRole"
}
}
}
Example: Using JSON Keys with Dots With IBM Connector Configuration
This example shows how to configure IBM MQ Connector using JSON keys with dots in their names:
<ibm-mq:config name="IBM_MQ_Config" doc:name="IBM MQ Config">
<ibm-mq:connection username="#[${aws-secrets::mySecretName}.'myProject.example.user']" password="#[${aws-secrets::mySecretName}.'myProject.example.pass']">
<ibm-mq:connection-mode>
<ibm-mq:client host="localhost" queueManager="QM1" channel="dummyChannel"/>
</ibm-mq:connection-mode>
</ibm-mq:connection>
</ibm-mq:config>Configure AWS Secrets Manager as a String
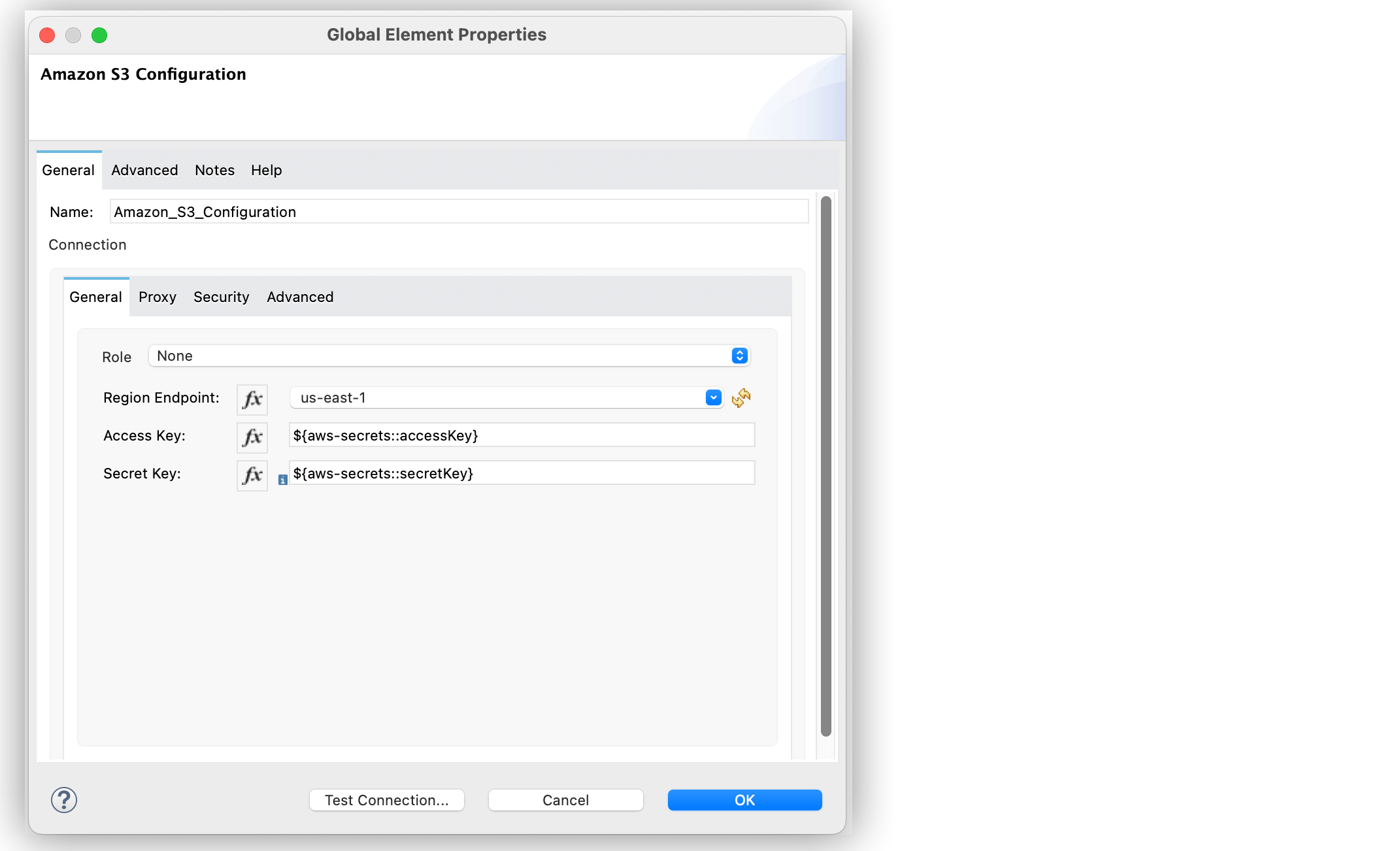
The following example shows how to configure the secret manager keys as a string for Amazon S3 Connector.
Based on the following string:
aws secretsmanager create-secret --name accessKey --secret-string "ACCESSKEY" aws secretsmanager create-secret --name secretKey --secret-string "SECRET"
In the Amazon S3 Configuration global element properties window:
-
Set Access Key to
${aws-secrets::accessKey}. -
Set Secret Key to
${aws-secrets::secretKey}.
In the Configuration XML editor, the configuration looks like this:
<s3:config name="Amazon_S3_Configuration" doc:name="Amazon S3 Configuration" >
<s3:connection accessKey="${aws-secrets::accessKey}" secretKey="${aws-secrets::secretKey}" />
</s3:config>Avoid using the $ special character in values stored in the secret manager. If you must use the $ character, use the variable in literal mode, which treats it as a string. After that, you can convert the entire value to JSON and extract the required information.



