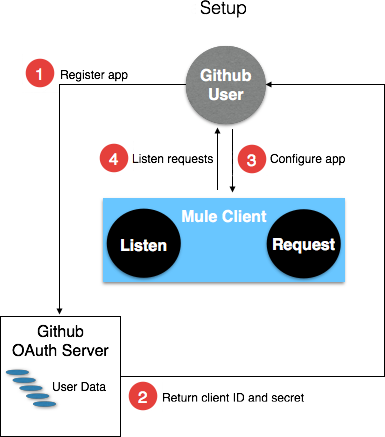
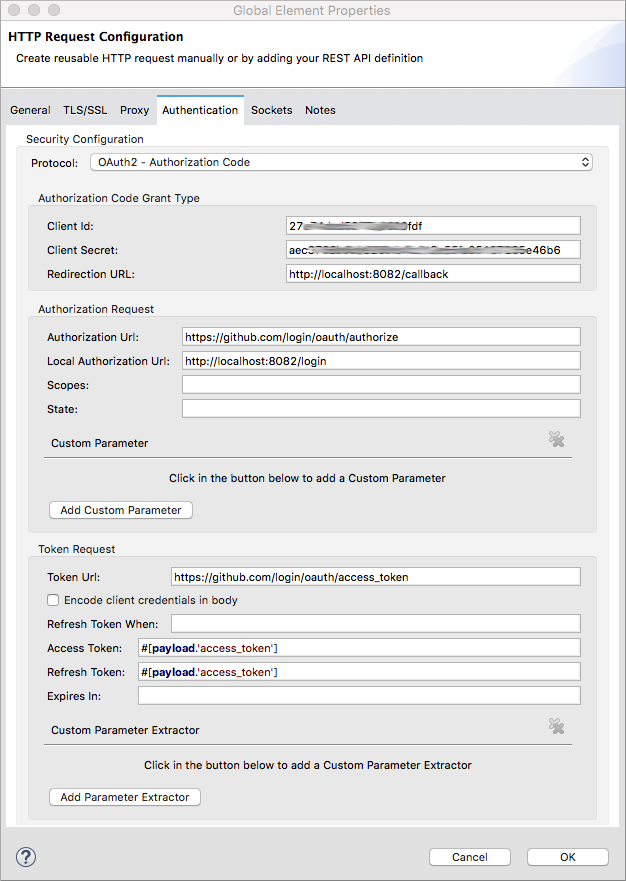
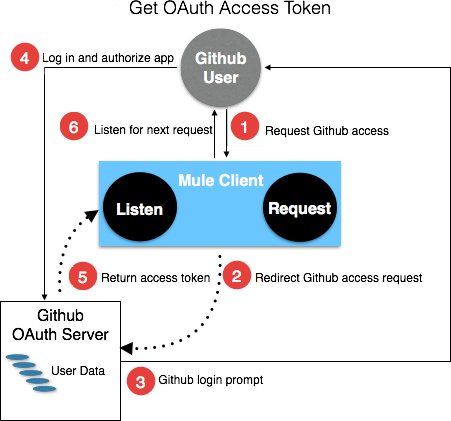
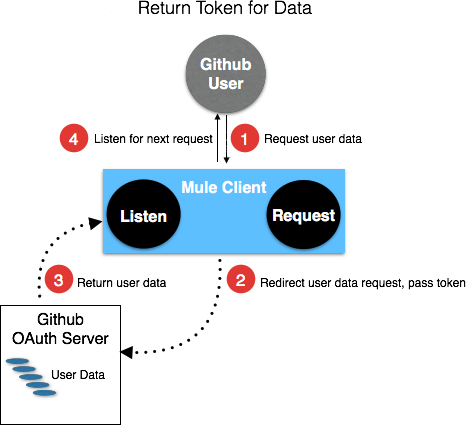
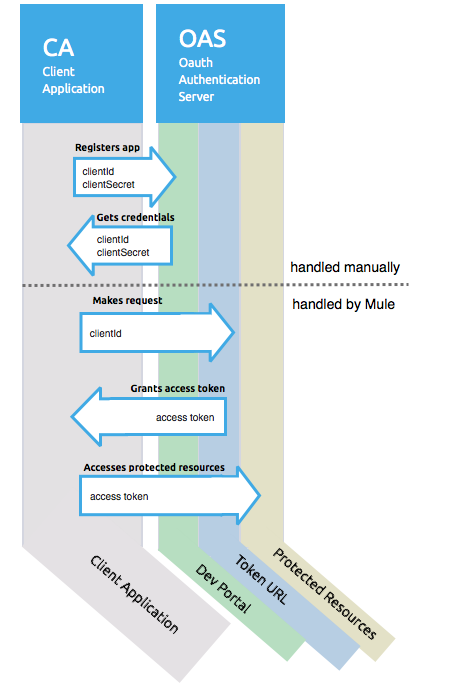
Studio Visual Editor
-
In Studio, create a new Mule project: File > New > Mule Project. The New Mule Project dialog appears.
-
In Project Settings, set the following options for the HTTP Listen Connector:
-
Project Name:
myproject -
Runtime: Select or accept the default
Mule Server 3.8.0 EEor later.
-
-
Drag an HTTP component from the palette to the Source section of the flow.
-
In the properties editor, accept the default Path
/and set Allowed Methods to GET. -
In Connector Configuration, click
 .
.The HTTP Listen Configuration dialog appears.
-
Click OK to accept the following options:
-
Name: HTTP_Listen_Configuration
-
Protocol: HTTP
-
Host: 0.0.0.0
-
Port: 8081
-
-
Click OK.
-
Save changes.
The error indicator disappears.
Next, set up an HTTP Request connector:
-
Drag another HTTP connector from the palette, and drop it in the Process area of the flow.
-
In the properties editor, in Connector Configuration, click
 .
.The HTTP Request Configuration dialog appears.
-
Set the following HTTP Request Configuration options:
-
Name: Accept
HTTP_Request_Configuration. -
Protocol: HTTPS
-
Host:
api.github.com -
Port:
443
-
-
On the Authentication tab, select Basic protocol.
-
In Username, type your Github user name.
-
In Password, type either your Github password or a personal access token
.
-
Check the Preemptive check box, and click OK.
The pre-emptive option passes the user name and password without waiting for a prompt from the server.
-
In the properties editor, set the following options for the HTTP Request connector:
-
Path:
/user -
Method: Select GET from the drop-down.
-
-
Save changes.
Format the output in JSON:
-
Drag a Transform Message component from the palette to the right of the HTTP request component.
-
In the properties editor, change the output of the payload as follows:
%dw 1.0 %output application/json --- payload
Finally, run the app:
-
Right-click the project name in project explorer, and choose Run as > Mule Application.
The console shows that the app is deployed.
-
Call the app using the following URL in a browser:
http://localhost:8081/The Github API returns your user information.
{ "login":"kahn", "id":16xxx343,"avatar_url":"https://avatars.githubusercontent.com/u/16xxx343?v=3"` ... }
XML Editor
<?xml version="1.0" encoding="UTF-8"?>
...
<http:listener-config name="HTTP_Listener_Configuration" host="0.0.0.0" port="8081" doc:name="HTTP Listener Configuration"/>
<http:request-config name="HTTP_Request_Configuration" protocol="HTTPS" host="api.github.com" port="443" doc:name="HTTP Request Configuration">
<http:basic-authentication username="kahn" password="7e5....921" preemptive="true"/>
</http:request-config>
<flow name="myprojectFlow">
<http:listener config-ref="HTTP_Listener_Configuration" path="/" doc:name="HTTP"/>
<http:request config-ref="HTTP_Request_Configuration" path="/user" method="GET" doc:name="HTTP"/>
<dw:transform-message doc:name="Transform Message">
<dw:set-payload><![CDATA[%dw 1.0
%output application/json
---
payload]]></dw:set-payload>
</dw:transform-message>
</flow>
</mule>xml