JCE Cryptography
The JCE strategy enables you to use the wider range of cryptography capabilities provided by the Java Cryptography Extension.
You can use cryptography capabilities in two ways:
-
Password-based encryption (PBE):
This method enables you to encrypt and sign content by providing only an encryption password. -
Key-based encryption:
Similar to how PGP and XML encryption works, this method enables you to configure a symmetric or asymmetric key to perform encryption and signing operations.
You can encrypt all, or part of a message using any of these two methods.
PBE
This method applies a hash function over the provided password to generate a symmetric key that is compatible with standard encryption algorithms. Because PBE only requires a password, a global configuration element is not needed for the PBE operations.
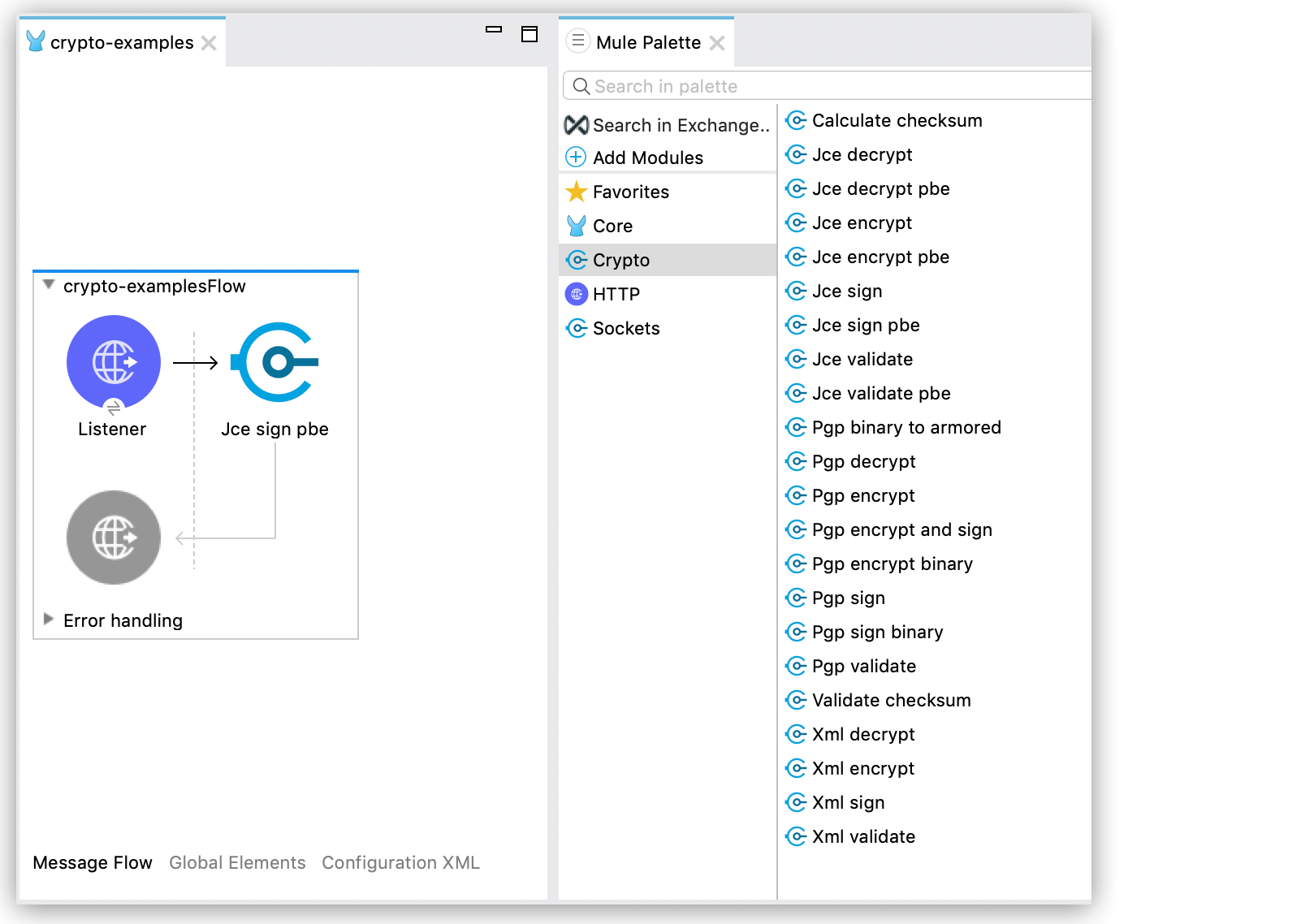
Configure Password-Based Encryption from Anypoint Studio
To configure PBE from Anypoint Studio, follow these steps:
-
From the Mule palette, add Crypto to your project.
See Install the Extension for instructions.
-
Select the desired operation, and drag the component to the flow:

-
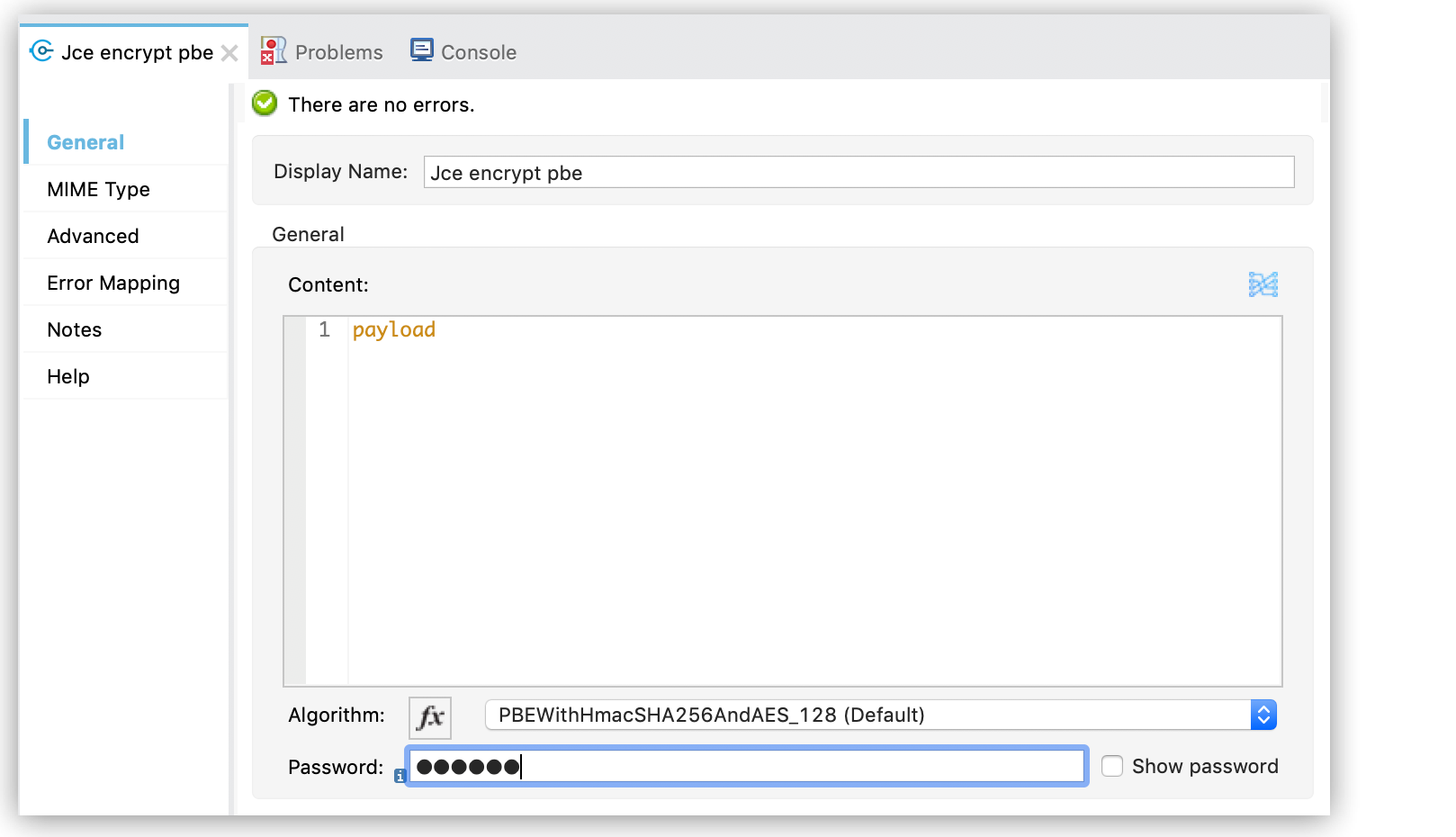
In the component view, configure the Algorithm and Password properties:
XML Examples
The following are XML examples for each each of the PBE operations:
-
PBE Encryption
<crypto:jce-encrypt-pbe password="a-Sup3r_Secure-Passw0rd"/>If no algorithm is specified,
PBEWithHmacSHA256AndAES_128is used. -
PBE Decryption
<crypto:jce-decrypt-pbe algorithm="PBEWithHmacSHA256AndAES_128" password="a-Sup3r_Secure-Passw0rd"/> -
PBE Signature
<crypto:jce-sign-pbe password="a-Sup3r_Secure-Passw0rd"/>If no algorithm is specified,
PBEWithHmacSHA256is used. -
PBE Signature Validation
<crypto:jce-validate-pbe password="a-Sup3r_Secure-Passw0rd" algorithm="PBEWithHmacSHA256" expected="#[vars.expectedSignature]"/>The
expectedparameter defines the signature used to validate the message.
Key-Based Encryption
Configure a symmetric or asymmetric key to perform encryption and signing operations.
Configure Key-Based Encryption from Anypoint Studio
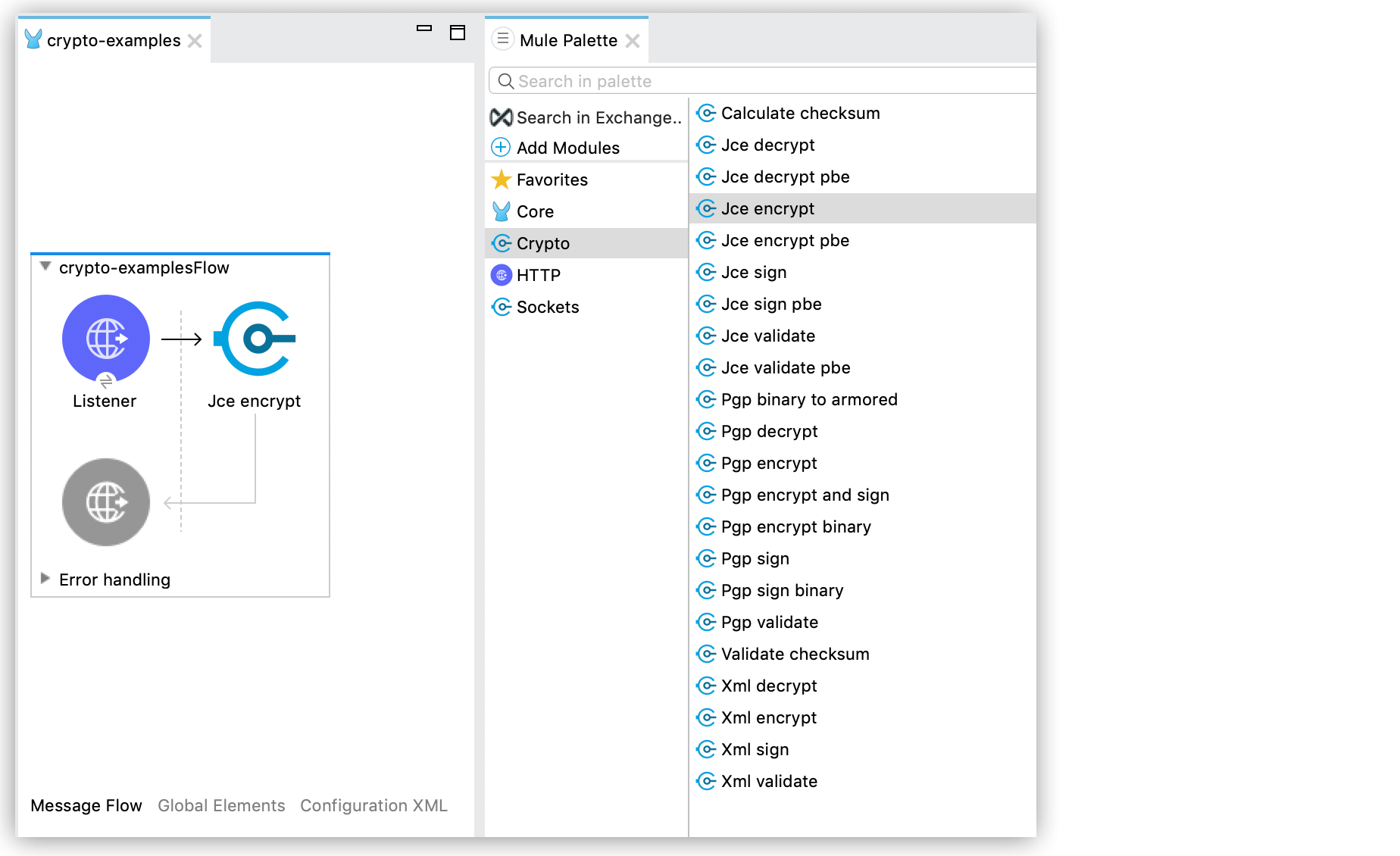
To configure key-based encryption operations from Anypoint Studio, follow these steps:
-
From the Mule palette, add Crypto to your project.
See Install the Extension for instructions.
-
Select the desired operation, and drag the component to the flow:
-
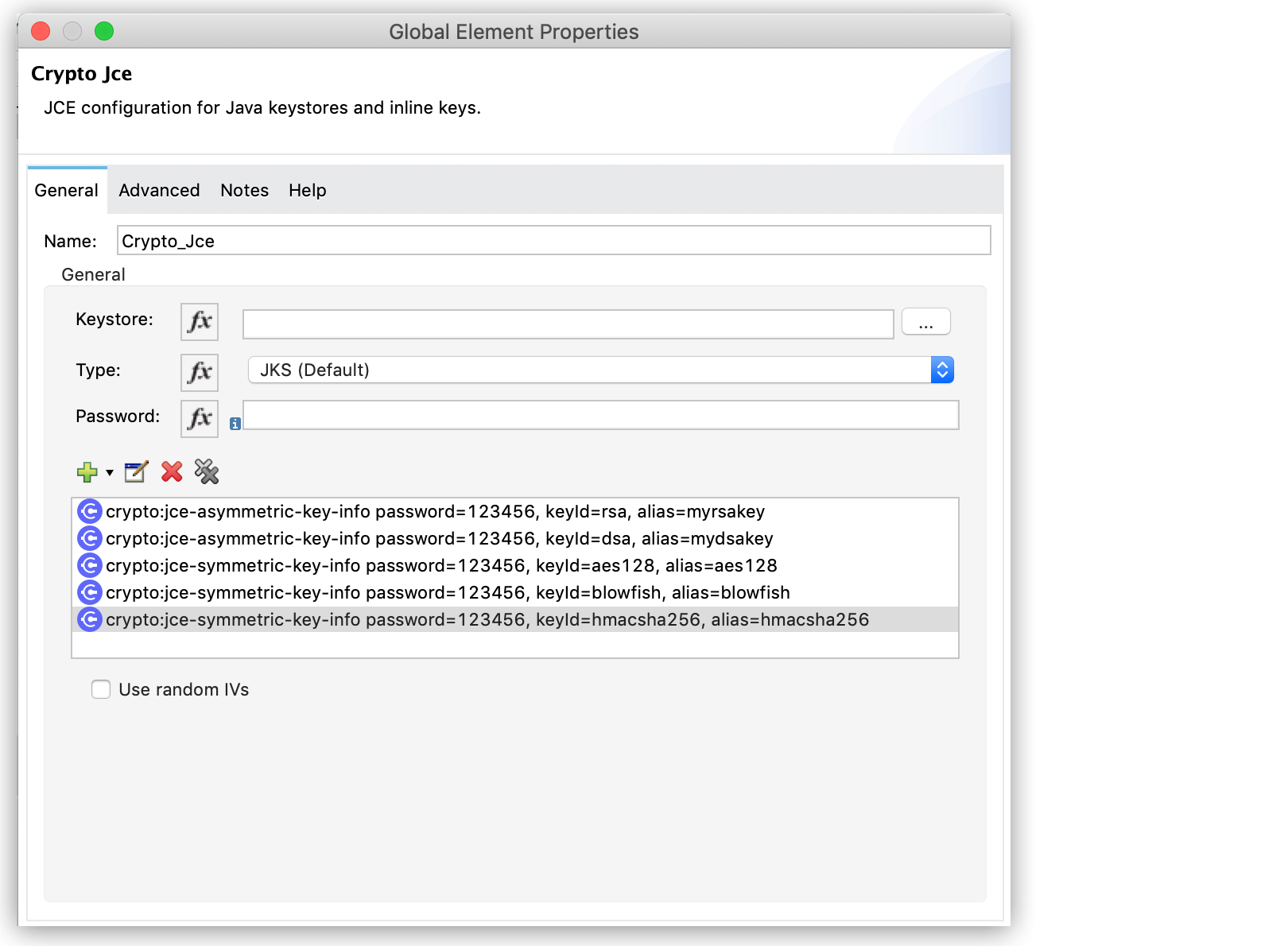
Open the component properties and select an existing module configuration, or create a new one by specifying values for Keystore, Type (JKS, JCEKS, PKCS12), and Password.
You can also add symmetric or asymmetric key information to be used in the sign operations:
-
Configure Key selection by using a Key id value previously defined in the module configuration, or define a new one for this operation:
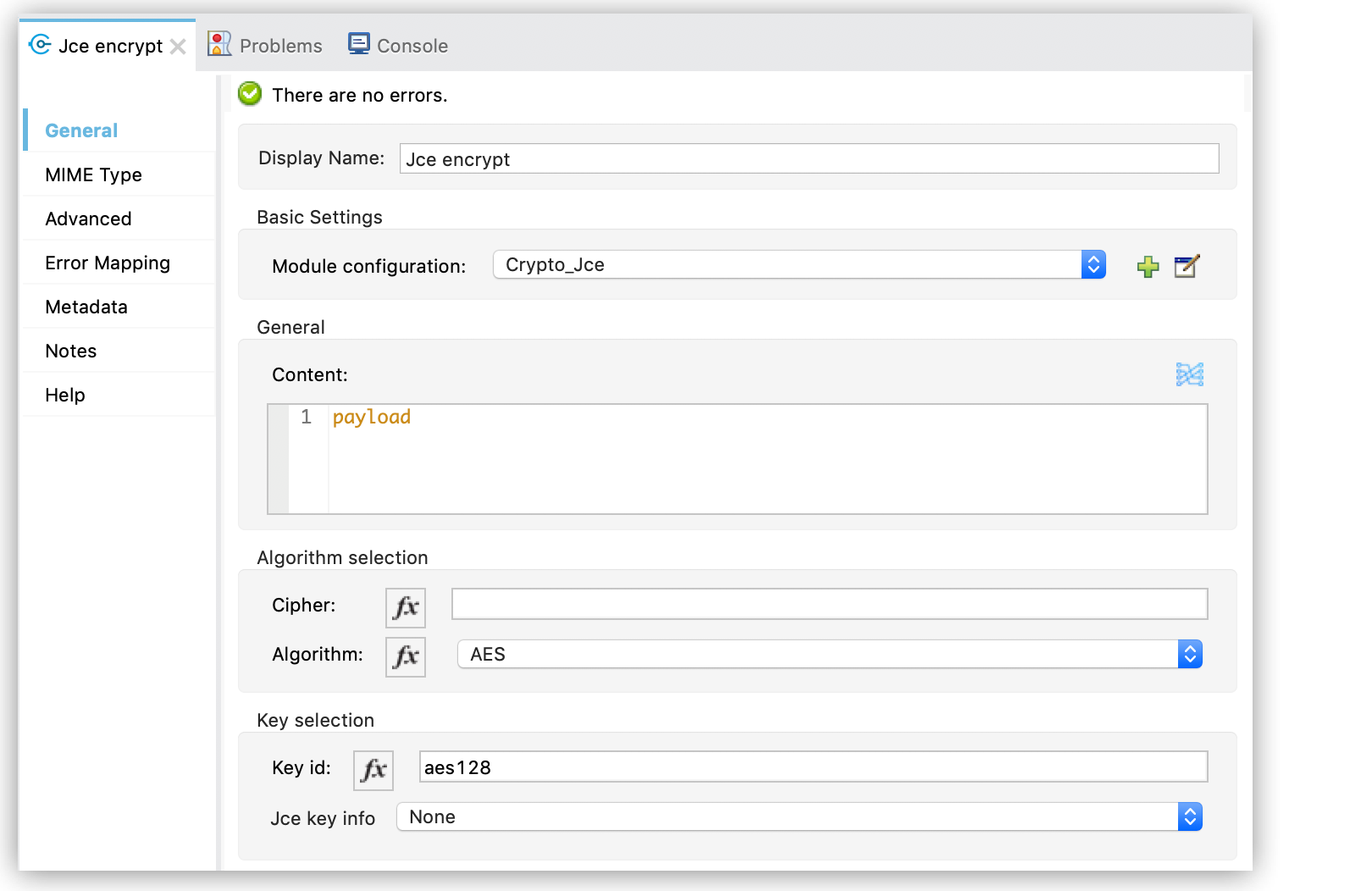
-
Select the algorithm to use during the operation.
XML Examples
The following XML examples show a JCE configuration that defines symmetric and asymmetric keys and different operations using these keys.
-
Configuration
In this example, a keystore with different types of keys is defined in a JCE configuration:
<crypto:jce-config name="jceConfig" keystore="jce/keys.jceks" password="123456" type="JCEKS"> <crypto:jce-key-infos> <crypto:jce-symmetric-key-info keyId="aes128" alias="aes128" password="123456"/> <crypto:jce-symmetric-key-info keyId="blowfish" alias="blowfish" password="123456"/> <crypto:jce-symmetric-key-info keyId="hmacsha256" alias="hmacsha256" password="123456"/> <crypto:jce-asymmetric-key-info keyId="rsa" alias="myrsakey" password="123456"/> <crypto:jce-asymmetric-key-info keyId="dsa" alias="mydsakey" password="123456"/> </crypto:jce-key-infos> </crypto:jce-config> -
Asymmetric Encryption
The following example operations use the asymmetric keys defined in the previous configuration.
Encrypting a Message<crypto:jce-encrypt config-ref="jceConfig" keyId="rsa" algorithm="RSA"/>Decrypting a Message<crypto:jce-decrypt config-ref="jceConfig" keyId="rsa" algorithm="RSA"/> -
Symmetric Encryption
The following example operations use the symmetric keys defined in the previous configuration.
Encrypting a Message<crypto:jce-encrypt config-ref="jceConfig" keyId="aes128" algorithm="AES"/>Decrypting a Message<crypto:jce-decrypt config-ref="jceConfig" keyId="aes128" algorithm="AES"/> -
Signature and Validation
The following are examples of sign and validate operations that use a key defined in the previous configuration:
Signing a Message<crypto:jce-sign config-ref="jceConfig" keyId="dsa" algorithm="SHA256withDSA"/>Validating a Signature<crypto:jce-validate config-ref="jceConfig" keyId="dsa" algorithm="SHA256withDSA" expected="#[vars.expectedSignature]"/>The
expectedparameter defines the signature used to validate the message.
Reference
Module Configuration
JCE configuration for Java keystores and inline keys.
Parameters
| Name | Type | Description | Default Value | Required |
|---|---|---|---|---|
Name |
String |
The name for this configuration. Connectors reference the configuration with this name. |
x |
|
Keystore |
String |
Path to the keystore file. |
X |
|
Type |
Enumeration, one of:
|
Type of the keystore. |
|
|
Password |
String |
Password for unlocking the keystore. |
|
|
Jce Key Infos |
Array of One of: |
List of keys to be considered, with internal IDs for referencing them. |
|
|
Expiration Policy |
Configures the minimum amount of time that a dynamic configuration instance can remain idle before the runtime considers it eligible for expiration. This does not mean that the platform will expire the instance at the exact moment that it becomes eligible. The runtime will actually purge the instances when it sees it fit. |
|
Jce Decrypt Operation
<crypto:jce-decrypt>
Decrypt a stream using JCE, with a key.
Parameters
| Name | Type | Description | Default Value | Required |
|---|---|---|---|---|
Configuration |
String |
The name of the configuration to use. |
x |
|
Content |
Binary |
You can decrypt all, or part of a message by using a DataWeave expression. |
|
|
Output Mime Type |
String |
The mime type of the payload that this operation outputs. |
|
|
Output Encoding |
String |
The encoding of the payload that this operation outputs. |
|
|
Streaming Strategy |
|
Configure if repeatable streams should be used and their behavior |
|
|
Cipher |
String |
A raw cipher string in the form "algorithm/mode/padding" according to the Java crypto documentation, for example |
|
|
Algorithm |
Enumeration, one of:
|
Algorithm from a list of valid definitions. When you specify this field, Mule automatically selects the mode and padding to use according to the following list:
|
|
|
Key Id |
String |
The key ID, as defined in the JCE configuration. |
|
|
Jce Key Info |
An inline key definition. |
|
||
Target Variable |
String |
The name of a variable on which the operation's output will be placed |
|
|
Target Value |
String |
An expression that will be evaluated against the operation's output and the outcome of that expression will be stored in the target variable |
|
|
Jce Encrypt Operation
<crypto:jce-encrypt>
Encrypt a stream using JCE, with a key.
Parameters
| Name | Type | Description | Default Value | Required |
|---|---|---|---|---|
Configuration |
String |
The name of the configuration to use. |
x |
|
Content |
Binary |
You can encrypt all, or part of a message by using a DataWeave expression. |
|
|
Output Mime Type |
String |
The mime type of the payload that this operation outputs. |
|
|
Output Encoding |
String |
The encoding of the payload that this operation outputs. |
|
|
Streaming Strategy |
|
Configure if repeatable streams should be used and their behavior |
|
|
Cipher |
String |
A raw cipher string in the form "algorithm/mode/padding" according to the Java crypto documentation, for example |
|
|
Algorithm |
Enumeration, one of:
|
Algorithm from a list of valid definitions. When you specify this field, Mule automatically selects the mode and padding to use according to the following list:
|
|
|
Key Id |
String |
The key ID, as defined in the JCE configuration. |
|
|
Jce Key Info |
An inline key definition. |
|
||
Target Variable |
String |
The name of a variable on which the operation's output will be placed |
|
|
Target Value |
String |
An expression that will be evaluated against the operation's output and the outcome of that expression will be stored in the target variable |
|
|
Jce Sign Operation
<crypto:jce-sign>
Sign a stream using JCE, with a key.
Parameters
| Name | Type | Description | Default Value | Required |
|---|---|---|---|---|
Configuration |
String |
The name of the configuration to use. |
x |
|
Content |
Binary |
The content to sign |
|
|
Algorithm |
Enumeration, one of:
|
The algorithm used for signing |
|
|
Output Mime Type |
String |
The mime type of the payload that this operation outputs. |
|
|
Key Id |
String |
The key ID, as defined in the JCE configuration. |
|
|
Jce Key Info |
An inline key definition. |
|
||
Target Variable |
String |
The name of a variable on which the operation's output will be placed |
|
|
Target Value |
String |
An expression that will be evaluated against the operation's output and the outcome of that expression will be stored in the target variable |
|
|
Jce Validate Operation
<crypto:jce-validate>
Validate a stream against a signature, using a key.
Parameters
| Name | Type | Description | Default Value | Required |
|---|---|---|---|---|
Configuration |
String |
The name of the configuration to use. |
x |
|
Value |
Binary |
the message to authenticate |
|
|
Expected |
String |
the signature to validate |
x |
|
Algorithm |
Enumeration, one of:
|
The algorithm used for signing |
|
|
Key Id |
String |
The key ID, as defined in the JCE configuration. |
|
|
Jce Key Info |
An inline key definition. |
|
Jce Decrypt Pbe Operation
<crypto:jce-decrypt-pbe>
Decrypt a stream using JCE, with a password.
Parameters
| Name | Type | Description | Default Value | Required |
|---|---|---|---|---|
Content |
Binary |
You can decrypt all, or part of a message by using a DataWeave expression. |
|
|
Algorithm |
Enumeration, one of:
|
The algorithm for generating a key from the password |
|
|
Password |
String |
The password for decryption |
x |
|
Output Mime Type |
String |
The mime type of the payload that this operation outputs. |
|
|
Output Encoding |
String |
The encoding of the payload that this operation outputs. |
|
|
Streaming Strategy |
|
Configure if repeatable streams should be used and their behavior |
|
|
Target Variable |
String |
The name of a variable on which the operation's output will be placed |
|
|
Target Value |
String |
An expression that will be evaluated against the operation's output and the outcome of that expression will be stored in the target variable |
|
|
Jce Encrypt Pbe Operation
<crypto:jce-encrypt-pbe>
Encrypt a stream using JCE, with a password.
Parameters
| Name | Type | Description | Default Value | Required |
|---|---|---|---|---|
Content |
Binary |
You can encrypt all, or part of a message by using a DataWeave expression. |
|
|
Algorithm |
Enumeration, one of:
|
The algorithm for generating a key from the password |
|
|
Password |
String |
The password for encryption |
x |
|
Output Mime Type |
String |
The mime type of the payload that this operation outputs. |
|
|
Output Encoding |
String |
The encoding of the payload that this operation outputs. |
|
|
Streaming Strategy |
|
Configure if repeatable streams should be used and their behavior |
|
|
Target Variable |
String |
The name of a variable on which the operation's output will be placed |
|
|
Target Value |
String |
An expression that will be evaluated against the operation's output and the outcome of that expression will be stored in the target variable |
|
|
Jce Sign Pbe Operation
<crypto:jce-sign-pbe>
Sign a stream using JCE, with a key.
Parameters
| Name | Type | Description | Default Value | Required |
|---|---|---|---|---|
Content |
Binary |
the content to sign |
|
|
Algorithm |
Enumeration, one of:
|
The algorithm used for signing |
|
|
Password |
String |
The password used to sign |
x |
|
Output Mime Type |
String |
The mime type of the payload that this operation outputs. |
|
|
Target Variable |
String |
The name of a variable on which the operation's output will be placed |
|
|
Target Value |
String |
An expression that will be evaluated against the operation's output and the outcome of that expression will be stored in the target variable |
|
|
Jce Validate Pbe Operation
<crypto:jce-validate-pbe>
Validate a stream against a signature, using a key.
Parameters
| Name | Type | Description | Default Value | Required |
|---|---|---|---|---|
Value |
Binary |
the message to authenticate |
|
|
Expected |
String |
the signature to validate |
x |
|
Algorithm |
Enumeration, one of:
|
The algorithm used for signing |
|
|
Password |
String |
The password used to sign |
x |
Types Definition
Expiration Policy
| Field | Type | Description | Default Value | Required |
|---|---|---|---|---|
Max Idle Time |
Number |
A scalar time value for the maximum amount of time a dynamic configuration instance should be allowed to be idle before it’s considered eligible for expiration |
||
Time Unit |
Enumeration, one of:
|
A time unit that qualifies the maxIdleTime attribute |
Repeatable In Memory Stream
| Field | Type | Description | Default Value | Required |
|---|---|---|---|---|
Initial Buffer Size |
Number |
This is the amount of memory that will be allocated in order to consume the stream and provide random access to it. If the stream contains more data than can be fit into this buffer, then it will be expanded by according to the |
||
Buffer Size Increment |
Number |
This is by how much will be buffer size by expanded if it exceeds its initial size. Setting a value of zero or lower will mean that the buffer should not expand, meaning that a |
||
Max Buffer Size |
Number |
This is the maximum amount of memory that will be used. If more than that is used then a |
||
Buffer Unit |
Enumeration, one of:
|
The unit in which all these attributes are expressed |
Repeatable File Store Stream
| Field | Type | Description | Default Value | Required |
|---|---|---|---|---|
Max In Memory Size |
Number |
Defines the maximum memory that the stream should use to keep data in memory. If more than that is consumed then it will start to buffer the content on disk. |
||
Buffer Unit |
Enumeration, one of:
|
The unit in which maxInMemorySize is expressed |
JCE PBE Encrypt and Decrypt
When using the JCE PBE Encrypt or Decrypt operations, consider the following specifications:
-
The length of the initialization vector (IV) is the cipher block size returned when calling
javax.crypto.Cipher.getBlockSize(). For example, if you use AES 128, then the block size is 16 bytes, so the IV has a length of 16 bytes. -
The key is generated from the password with 0 iterations and a null salt value for encrypt and decrypt. For signing and validation, the Mac is generated with 20 iterations and a fixed salt value hardcoded in the connector’s code.



