Configuring Security for Anypoint Platform PCE
To use Anypoint Platform Private Cloud Edition (Anypoint Platform PCE), you must supply TLS credentials. Upload a certificate via the Anypoint Platform UI under Access Management, and configure the platform to use this certificate to secure communications. Ensure that every machine connected to the platform, including Mule runtime engine (Mule), trusts this certificate. Additionally, you have the option to specify custom ciphers and Diffie-Hellman (DH) groups for the key exchange method if needed.
When you replace or change the certificate, Anypoint Platform restarts the nginx server.

To configure the security, follow these steps:
-
Create a certificate.
Generate your certificate using a tool like OpenSSL. To be compatible with Anypoint Platform, ensure your certificate is in an
nginxfriendly format. The certificate must include the domain name of your installation as both the Common Name (CN) and the Subject Alternative Name (SAN). -
From Anypoint Platform, select Access Management.
-
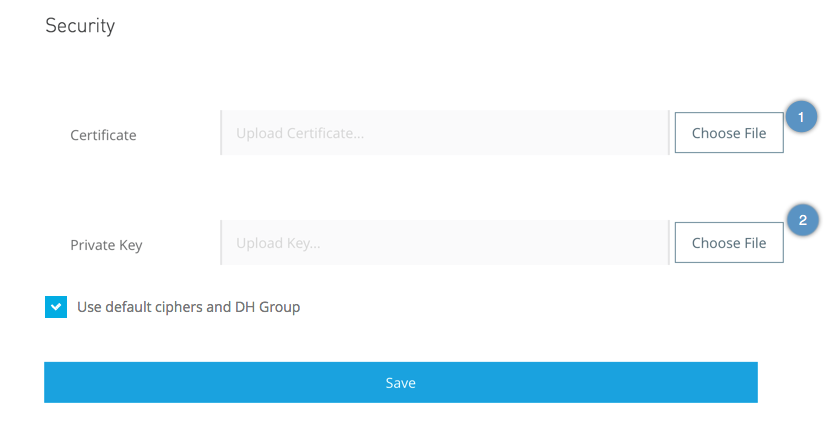
Select Security.
-
Under Certificate, select Browse to select the certificate on your local system.
-
Under Key, select Browse to select the private key for your certificate.
-
For additional security, you can upload your own cipher and Diffie-Hellman group file.
Note that this step is optional.
-
Deselect Use default ciphers and DH Group.
-
Enter a set of ciphers from the list of valid NGINX ciphers. If you are using Open SSL, you can view this list by running the
openssl cipherscommand. The cipher you enter must be in annginxcompatible format, for example:ECDHE-RSA-AES256-GCM-SHA512:DHE-RSA-AES256-GCM-SHA512:ECDHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-SHA384
-
Generate
dhparam.pem(the Diffie-Hellman group file) using the followingopensslcommand:openssl dhparam 2048 -out dhparam.pem
-
Upload the
dhparam.pemfile from your system.
-



