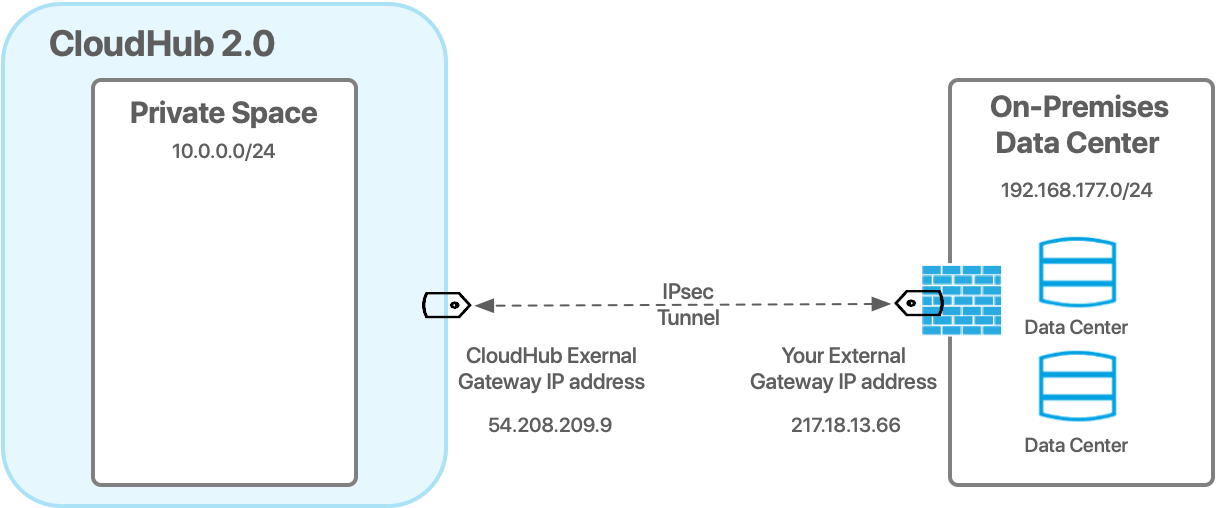
Anypoint Virtual Private Network
Anypoint VPN (virtual private network) creates a secure connection between your private space and your on-premises network. Anypoint VPN enables apps running in the private space to access resources in your on-premises data centers behind your corporate firewall.
You can create multiple site-to-site VPNs if required.
| The number of VPNs you can create depends on the network connection entitlements available to your account. Contact your MuleSoft account representative if you don’t know how many network connection entitlements you have on your account. |
Anypoint VPN supports site-to-site Internet Protocol security (IPsec) connections between the private space and the VPN endpoint, a gateway device, a physical or software appliance located in your network.
The MuleSoft side of the connection is an implementation of a virtual private gateway (VGW). The MuleSoft VGW is associated with a single private space but can support up to 10 VPN connections.
| MuleSoft implementation capabilities might vary from other VGW offerings. |

To create an Anypoint VPN connection to your network, see Create a Connection to an External Network.
Anypoint VPN Features
Each Anypoint VPN connection consists of two tunnels that enable you to connect to a single public IP address at a remote location. To configure connectivity to an additional public IP address at a remote location, you must create two VPN connections.
Routine maintenance can briefly disable one of the two tunnels of your VPN connection. Your VPN connection automatically fails over to the second tunnel during this time, so access is not interrupted. For this reason, you must configure both tunnels on your endpoint. Tunnel selection depends on your VPN endpoint capabilities and the routing type selection.
The MuleSoft VGW implementation supports a maximum throughput of 1.25 Gbps. Multiple VPN connections to the same private space share the throughput capabilities of a single VGW. The VPN connection throughput depends on several factors, such as the capability of your VPN endpoint, the capacity of the connection, the average packet size, the protocol, and network latency between the gateways.
Anypoint VPN also supports high availability, wherein each Anypoint VPN connection consists of two endpoints to lessen the likelihood of connection failures.
IPsec Settings
Anypoint VPN supports any combination of the following IPsec settings:
-
IKE version 1
-
IKE version 2 for route-based VPNs only
-
AES 128 or 256-bit encryption operating in the CBC and GCM
-
SHA or SHA-2 (256, 384, 512) hashing
-
Diffie-Hellman Phase 1 groups 2, 14-24
-
Diffie-Hellman Phase 2 groups 2, 5, 14-24
-
Timeouts for IKEv1:
-
IKE (Phase 1) Lifetime: 28800 seconds (8 hours)
-
IPsec (Phase 2) Lifetime: 3600 seconds (1 hour)
-
-
Timeouts for IKEv2:
-
IKE (Phase 1) Lifetime: 28000 seconds (7 hours and 50 minutes)
-
IPsec (Phase 2) Lifetime: 3000 seconds (50 minutes)
-
Anypoint VPN Routing
Anypoint VPN supports dynamic or static routing for VPN connections.
- Dynamic routing
-
Your device uses Border Gateway Protocol (BGP) to advertise routes to Anypoint VPN.
Use BGP routing if your device supports this protocol.
- Static routing
-
You must specify the routes (subnets) in your network accessible through Anypoint VPN.
You can remove routes for static VPN connections.
Anypoint VPN Routing Limitations
-
A maximum of 95 route table entries is permitted per private space, regardless of the number of VPN connections.
To avoid exceeding the limit, consolidate networks to the fewest number possible.
-
You can’t add a route that matches a priority route (a route that your private network uses).
-
Only one connection can use a route at a time.
If you enter a non-local/Internet Gateway (IGW) route to a route table, CloudHub 2.0 warns that another connection uses the route.
-
Routes should not overlap with existing routes.
You receive a warning if you enter a route that overlaps with another route in the route table.
Anypoint VPN Limitations
Anypoint VPN does not support these features and configurations:
-
Network Address Translation (NAT)
-
IPv6
-
IKEv2 with policy-based VPNs
-
Advertising a default route (0.0.0.0/0) over BGP or static routing
Requirements for Static VPN Connections
To create a static VPN connection, your VPN endpoint must be able to:
-
Establish IKE Security Associations using a Pre-Shared Key (PSK)
-
Establish IPsec Security Associations in Tunnel mode
-
Use any combination of IPsec settings that MuleSoft supports
-
Fragment IP packets before encryption
You must fragment packets that are too large to transmit. Your VPN device must be able to fragment packets before encapsulation.
-
Use one Security Association (SA) pair per tunnel
Anypoint VPN supports one unique SA pair per tunnel (a pair refers to one inbound and one outbound connection). Some policy-based devices create an SA for each ACL (access-control list) entry. In this situation, you must consolidate your rules and then filter unwanted traffic.
-
Use IPsec Dead Peer Detection (DPD)
DPD allows devices to rapidly identify when network conditions change. You can enable DPD on the MuleSoft endpoint using
DPD Interval: 10andDPD Retries: 3. -
Allow asymmetric routing
Asymmetric routing occurs when routing policies send traffic from your network to the private space through one tunnel and traffic returns from the private space through the other tunnel. The MuleSoft VPN endpoint selects the tunnel using an internal algorithm, making the return path dynamic. If your device uses an active/active tunnel configuration, you must allow asymmetric routing for each Anypoint VPN connection.
-
For IPsec, enable perfect forward secrecy (PFS) with the above Phase 2 Diffie-Hellman groups
Requirements for Dynamic VPN Connections
To create a dynamic VPN connection, in addition to the static VPN connection requirements, the VPN endpoint must support:
-
Establishing BGP peering
-
Using route-based VPNs (bind tunnels to logical interfaces)
-
For IPsec, enabling perfect forward secrecy (PFS) with the above Phase 2 Diffie-Hellman groups
Anypoint VPN Recommendations
-
Adjust the maximum segment size of TCP packets entering the VPN tunnel.
VPN headers require additional space, which reduces the amount of space available for data.
To limit the impact of this behavior, configure your endpoint with TCP MSS Adjustment: 1387 bytes.
-
Reset the
DFflag on packets.Packets might carry a Don’t Fragment (
DF) flag, indicating that the packet must not be fragmented. Some VPN devices can override theDFflag and fragment packets unconditionally when required. If available, enable the settingClear Don’t Fragment (DF) Bit.
VPN High Availability
To ensure your applications and related operations are tolerant to Anypoint VPN updates or issues, or individual customer gateway failures, implement high availability VPN connections. Set up a redundant VPN connection to prevent losing connectivity if another VPN or connection device is unavailable and allow for maintenance downtime.
The redundant VPN inherits some settings from the initial VPN configuration automatically. For example, if the routing type for the initial VPN is dynamic (BGP), the redundant VPN is also dynamic.
Other settings for the redundant VPN, such as the remote ASN for dynamic routing, include the values from the initial VPN, but you can change the values.
To configure a redundant VPN connection, you must:
-
Have two VPN endpoints available in your network that use different public IP addresses.
Each gateway device supports a single VPN.
-
Create two VPN connections in your private space.
Configure High Availability with Anypoint VPN
The following example shows a high availability VPN topology using a single Anypoint VPC and two VPN connections.
A MuleSoft Virtual Private Gateway (VGW) supports one Anypoint VPC association, but it supports up to 10 VPN connections. You can locate your VPN Gateways in the same data center, or in different physical locations.
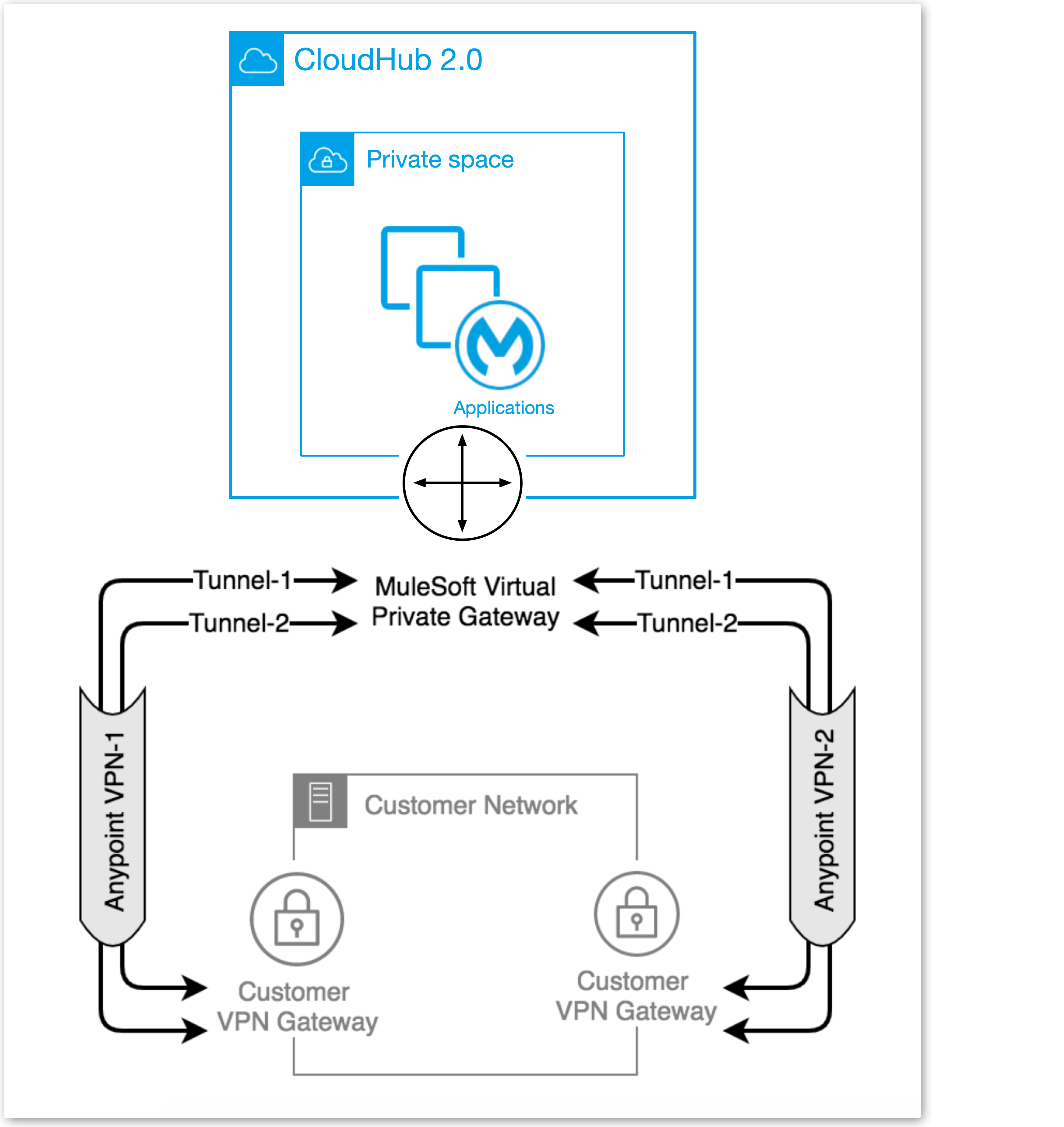
Use BGP routing to advertise the same routes via VPN-1 and VPN-2. See Anypoint VPN Path Selection using BGP Routing for instructions on how to control path selection via the routing protocol.
In this scenario, the VPN Gateways are configured to prefer: VPN-1 Tunnel-1, then VPN-1 Tunnel-2, then VPN-2 Tunnel-1, and finally VPN-2 Tunnel-2. This configuration produces an automatic failover to another tunnel, and to another VPN in the event of a VPN connectivity issue. This makes the Anypoint VPN solution more resilient and robust.
High availability VPN connections also support static routing, in which you establish a VPN-2 to work as a redundant, standby connection in the event of a failure with VPN-1.
How VPN Failover Works
Failover to a redundant VPN depends on the routing type:
-
Dynamic (BGP)
-
Static
Failover for dynamic or BGP VPNs is automatic. For static VPN failover, you must manually fail over to the other available VPN by modifying the routes.
VPN and Tunnel Status
New VPN connections that you create appear in the Connections section of the private space. Initially, both VPN tunnels display DOWN while the infrastructure is created.
Depending on your configuration, tunnels might report a status of DOWN during normal operations.
| Status | Tunnel 1/2 | Description |
|---|---|---|
|
|
The VPN connection is recently created, and actions are pending in the background. You might see this status for 10-15 minutes after creating a VPN. |
|
|
The VPN connection is created, but the remote side is not configured or is not sending traffic. |
|
|
The VPN connection is created, and the remote side established the connection successfully. Tunnels operate in active/active or active/passive mode, depending on the routing configuration and your VPN device type. |
|
|
The VPN connection is not created. Delete the VPN and try again. If this failure recurs, contact MuleSoft Support. |



