Query parameter
To Use a Mule Provider for OAuth 2.0 Authentication
You need to obtain the access token before attempting to send requests to the API protected by the OAuth 2.0 Access Token Enforcement Using External Provider policy. Include the token in all requests sent to the API using a query parameter or an authorization header as shown in the Postman example in the next procedure. The following table summarizes this usage:
| Places to include Token | Example | Notes |
|---|---|---|
|
Included as part of the URI |
|
Authorization header |
|
The header consists of a key:value pair, where Authorization is the key and the value is composed as follows:
|
When a request is received, the OAuth 2.0 Access Token Enforcement Using External Provider policy sends a request to the /validate URL of the OAuth provider to ensure the validity of the token.
To use and test authentication:
In this procedure, you build upon an earlier tutorial by applying the OAuth 2.0 Access Token Enforcement Using External Provider policy to the JSONPlaceholder service API. The RAML definition of an API needs to include a security scheme for OAuth 2.0. You can include any required RAML snippets in your API from the API Manager Available Policies list to enforce policies.
On the portal for the API, you request access to an API, and you receive credentials to access the JSONPlaceholder API from your application. You base64-encode the credentials that the application receives to access the API. Using the encoded credentials, you get an access token from the provider—steps 1-2 of the OAuth dance. Use the token to call the JSONPlaceholder service—steps 3-6 of the OAuth dance. If the token isn’t properly validated, a 403 error message is returned to the client application; otherwise, the API returns results, the list of users—step 7 of the OAuth dance.
-
Create and deploy the JSONPlaceholder service API proxy using API Manager.
You can download the RAML for creating the JSONPlaceholder service API.
-
In the RAML of JSONPlaceholder API, include the RAML snippet required by the OAuth 2.0 Access Token Enforcement policy. Add the authorization URI, access token URI, and authorization grants; add the securedBy node after the method name of the resource and method you want to secure, as shown in the following snippet:
#%RAML 1.0 title: placeholder version: 1.0.development baseUri: http://jsonplaceholder.typicode.com securitySchemes: oauth_2_0: description: | This API supports OAuth 2.0 for authenticating all API requests. type: OAuth 2.0 ... 403: description: | Bad OAuth request (wrong consumer key, bad nonce, expired timestamp...). Unfortunately, re-authenticating the user won't help here. settings: authorizationUri: https://auth-provider-testing.cloudhub.io/external/authorize accessTokenUri: https://auth-provider-testing.cloudhub.io/external/access_token authorizationGrants: [authorization_code, password, client_credentials, implicit] ... /users: get: securedBy: [oauth_2_0]yaml -
Apply the OAuth 2.0 Access Token Enforcement to the API.
-
Leave Scopes blank.
-
In Access Token validation endpoint url, use the URL of the provider with the validation path:
https://<your-provider-app-name>.cloudhub.io/external/validate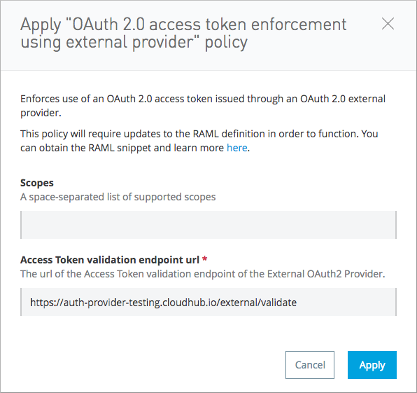
-
-
Create an API portal for the API.
-
Request access for a client application to the JSONplaceholder service API.
You obtain the client ID and client secret for a requesting application.
-
Encode the client ID and client secret in base64.
echo '<Client Id>:<Client Secret>' | base64 -
Use the encoded credentials to get an access token from the provider.
For example, assume the encoded credentials are YmQ2…UY5NkYK. Use this curl command to request the access token (Windows users need to download a
curltool):curl -i -X POST -H 'Content-Type: application/x-www-form-urlencoded' -H 'Authorization: Basic YmQ2...UY5NkYK' -d 'grant_type=password&username=max&password=mule' 'https://auth-provider-testing.cloudhub.io/external/access_token' -k
The provider returns the access token:
HTTP/1.1 200 Content-Type: application/json; charset=UTF-8 Date: Fri, 14 Oct 2016 21:41:44 GMT MULE_ENCODING: UTF-8 Server: nginx Content-Length: 250 Connection: keep-alive {"access_token":"Fy6l_dsnzVFoduMPS3xx6RUeraVDJlWT37ql7ngxFWkERZ9wq4Uy9J1GC57_vzzCGUCGOF0KVDCg6bR2qTQd7A","refresh_token":"Mx0LRTA7_N4TVdg86MXk0dRSIsSLRIcFcI3O9T0T_hy6MPhrjxA797ew-mGD0Nom-1CcTvU4CHOCLnOKSZfpAw","token_type":"bearer","expires_in":1800} -
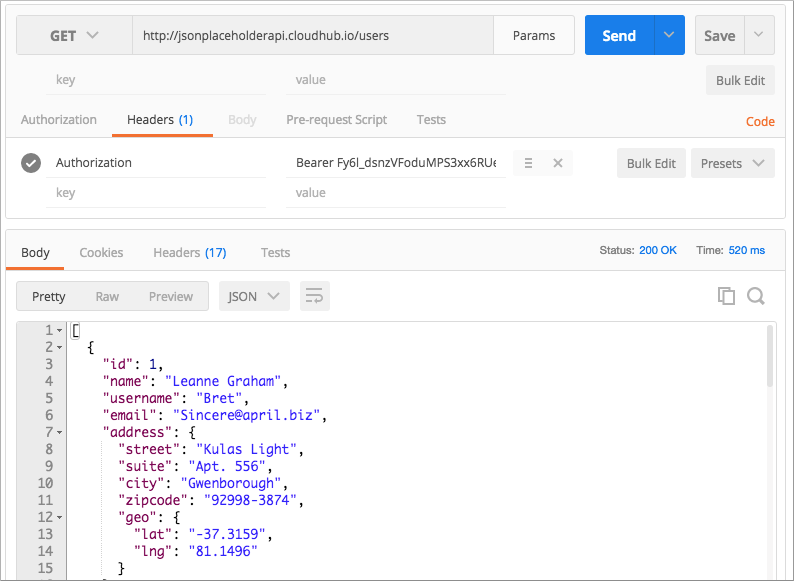
In Postman, use the access token to call the JSONPlaceholder service API:
-
Select the GET operation and enter the URL for the JSONPlaceholder service API to get the list of users:
http://jsonplaceholderapi.cloudhub.io/users. -
On the Headers tab, for the key, select Authorization. For the value, type
Bearerfollowed by the access token that the provider returned for the client application. -
Click Send.
The call succeeds and the API returns the list of JSONPlaceholder users.
-



