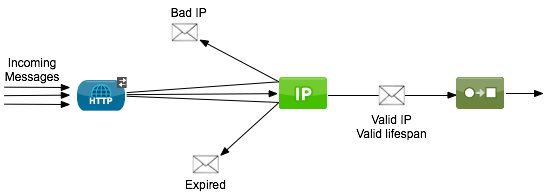
Anypoint Filter Processor
Generally positioned immediately after an inbound connector in a Mule flow, the Anypoint Filter Processor evaluates two message properties, and rejects the message if the values fall outside of its configured parameters.
The properties that are evaluated are:
-
IP address – If the IP address of a message falls outside the filter’s configured IP address range, Mule does not process the message (see image below).
-
Creation timestamps — Where the message’s creation date and time fall outside the filter’s configured acceptable lifespan (that is, the message is older than expected), Mule does not process the message (see image below).

Configuring the Anypoint Filter Processor
Use an Anypoint Filter Processor to protect a network, database, or system from unauthorized access by users outside the network. In other words, use a filter to exclude users from non-authorized IP addresses from accessing your system.
Further, use a security filter to protect your resource against a replay attack. By rejecting messages with a lifespan that exceeds a short timeframe — 30 seconds, for example — Mule protects your application from processing the same message a user maliciously sends multiple times. To be effective, a Mule flow should employ a digital signature, in addition to this type of security filter, to sign the creation time of the message.
| This topic introduces the idea of Global Elements; if you are unfamiliar with this functionality, access Understand Global Elements to learn more before proceeding. |
To configure the Anypoint Filter Processor to filter by IP address range:
-
Add a global Filter Element to your application and apply a unique Name to the element.
-
Place a Filter message processor in your flow, typically positioned after an inbound connector, such as HTTP, to filter out invalid messages early in the flow.
-
Configure the message processor according to the table below.
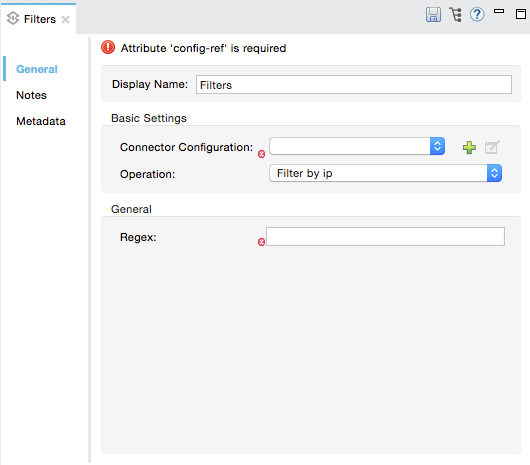
Field Required Value Display Name
Yes
A unique name for your message processor.
Config Reference
Yes
Use the name of the global element you created above.
Operation
Yes
Filter by ip
Regex
No
Enter a regex expression to apply further rules for filtering messages based on the IP address range.
-
Add a global
filters:configelement to your application, set above all the flows in your application. -
Configure the global element according to the table below.
Attribute Required Value name
Yes
A unique name for your element.
doc:name
Yes
A display name for the element in Studio’s Visual Editor. Not applicable for Standalone.
-
Place a
filters:filter-by-ipelement in your flow, typically positioned after an inbound connector, such as HTTP, so as to filter out invalid messages early in the flow. -
Configure the message processor according to the table below.
Field Required Value config-ref
Yes
Use the name of the global element you created above.
regex
No
Enter a regex expression to apply further rules for filtering messages based on the IP address range.
doc:name
Yes
A display name for the element in Studio’s Visual Editor. Not applicable for Standalone.
Filter Strategies
The Anypoint Filter processor allows you to filter messages according to the following four filter strategies:
| Operation | Description | Example |
|---|---|---|
Filter by ip |
Type an IP address or regular expression to define the address or range from which the Filter accepts connections. |
Examples: |
Filter by ip range |
Enter a net address and mask to determine the IP range. The IP addresses or ranges you enter are considered valid, and allowed by the Filter. |
Net: Mask: |
Filter by ip range cidr |
Enter the desired IP range in CIDR notation. |
Cidr: |
Filter expired |
This option allows you to define an expiration time for the message.
|
Expires in:
Expires in: |



