FIPS 140-2 Compliance Support
As of Mule 3.5.0, Mule can be configured to run in a FIPS 140-2 certified environment. Note that Mule does not run in FIPS security mode by default. There are two requirements:
-
Have a certified cryptography module installed in your Java environment
-
Adjust Mule settings to run in FIPS security mode
Prerequisites
This document assumes that you are familiar with FIPS 140-2, the US government security standard that requires that compliant parties use only cryptographic security modules that have been certified by NIST. This document also assumes that you have selected and obtained a certified security module
.
Setting Up a FIPS 140-2 Java Environment
Mule relies on the Java runtime to provide a FIPS-compliant security module, which is why the first requirement is to have a FIPS 140-2 Java environment properly set up. If you are setting up your system for FIPS compliance for the first time and you have not already configured a certified security provider, you must first select and obtain one, then set up your Java environment following the instructions specific to your selected provider.
Details for this process vary according to your selected security provider Please refer to the documentation for your security provider for complete instructions.
Running Mule in FIPS Security Mode
Next, set up your Mule instances to work in a FIPS 140-2-compliant environment by updating the configuration of the wrapper that launches the Mule application server.
-
Open your wrapper.conf file (located in $MULE_HOME/conf folder).
-
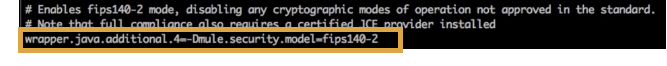
Uncomment the line that sets Mule to work in FIPS security mode, as shown. Be sure to replace the
<n>with the next sequential number in your wrapper.conf file.
-
Save.
When Mule next launches, the startup readout indicates that FIPS security mode is enabled.
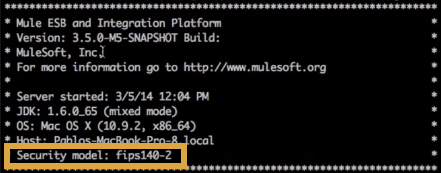
With FIPS security mode enabled, Mule automatically restricts protocol negotiations to use only the subset of approved cryptographic cipher suites. Any HTTPS connectors and any other connectors that use a TLS security layer will be automatically affected by this restriction.
Fine-Tuning SSL Connectors
The Mule conf folder includes two files that allow you to fine-tune the configuration of SSL connectors by manually setting which cipher suites Mule can use and which SSL protocols are allowed:
-
tls-default.conf(Allows fine-tuning when Mule is not configured to run in FIPS security mode) -
tls-fips140-2.conf(Allows fine-tuning when Mule is running in FIPS security mode)
Open the relevant file and comment or uncomment items in the lists to manually configure the allowed cipher suites and SSL protocols. If you make no changes to these files, Mule allows the configured security manager to select cipher suites and protocols.
Anypoint Enterprise Security and FIPS
Anypoint Enterprise Security version 1.3 supports FIPS security mode. When in FIPS security mode, Mule will not register a security provider, allowing the module to rely on the platform security provider.
Note that not all encryption schemes and signatures included in Anypoint Enterprise Security configuration options are FIPS compliant. If you see an error at runtime that reads, “Could not find encryption algorithm '<algorithm-name>'. You are running in FIPS mode, so please verify that the algorithm is compliant with FIPS” this means that your application is using an algorithm that is not approved for FIPS use. Adjust your configuration to select an approved algorithm. Keep in mind that your different environments may have different security configurations, including different encryption schemes and algorithm selections; thus you may see this error only in certain environments, depending on how they are set up.
Tips and Limitations
-
The Bouncy Castle security provider, which is bundled with the Mule distribution, is not FIPS certified. When Mule starts in FIPS security mode, the Bouncy Castle provider is not registered or used.
See Also
-
Access a full list of validated FIPS-2 Cryptographic Modules
.
-
Access a full list of approved cryptographic algorithms
.



