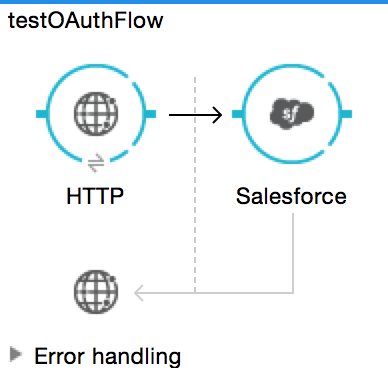
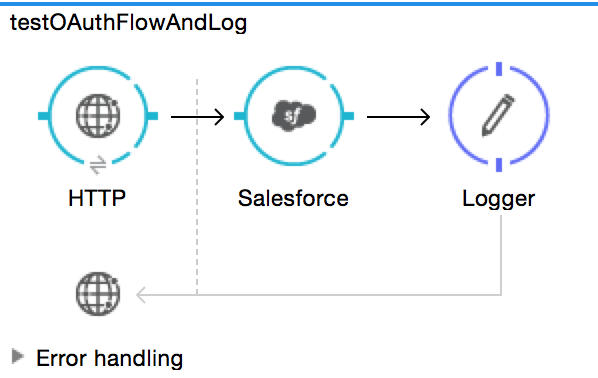
Studio Visual Editor
-
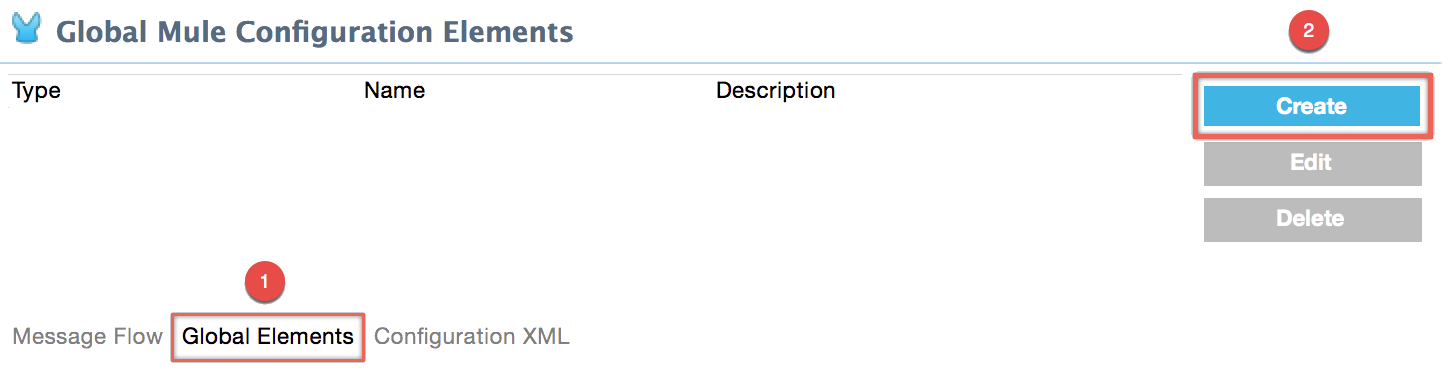
If you haven’t already done so, create a new Mule project, then click the Global Elements tab at the bottom of the canvas.
-
Click Create, then expand the Connector Configurations to show the available connectors.
-
Select the appropriate global type that matches your OAuth-enabled connector. Click OK.
-
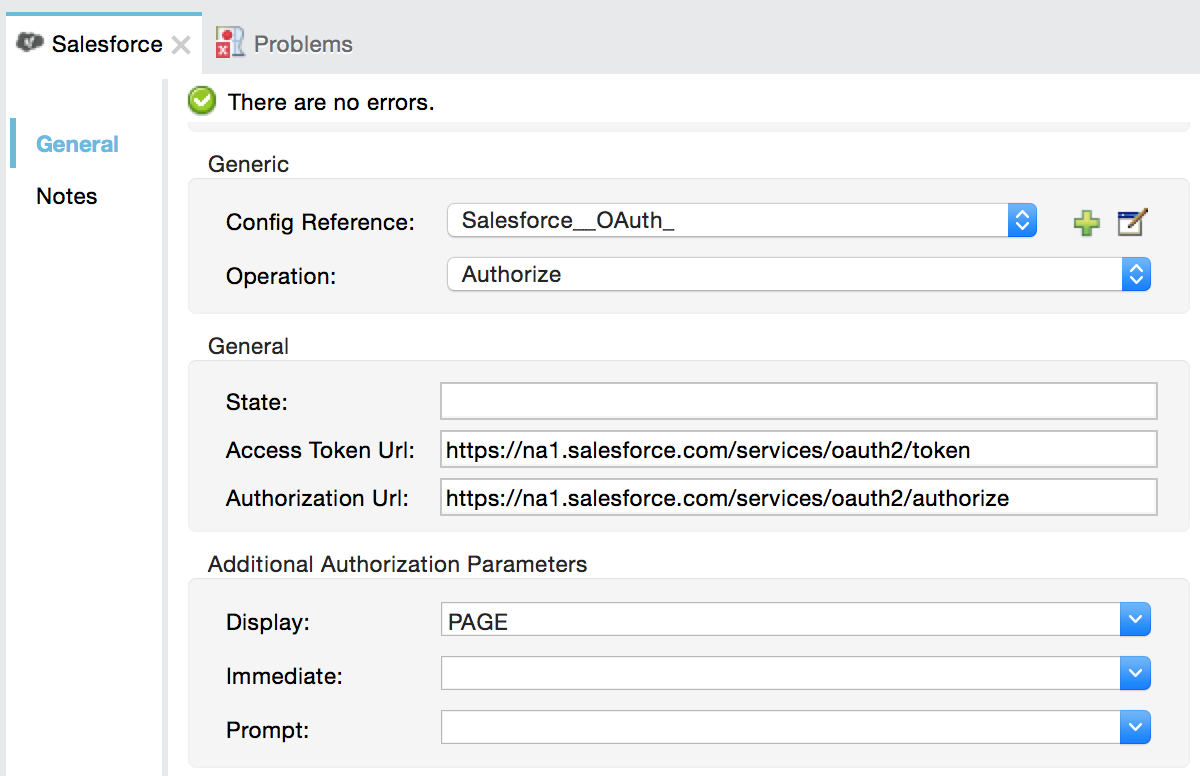
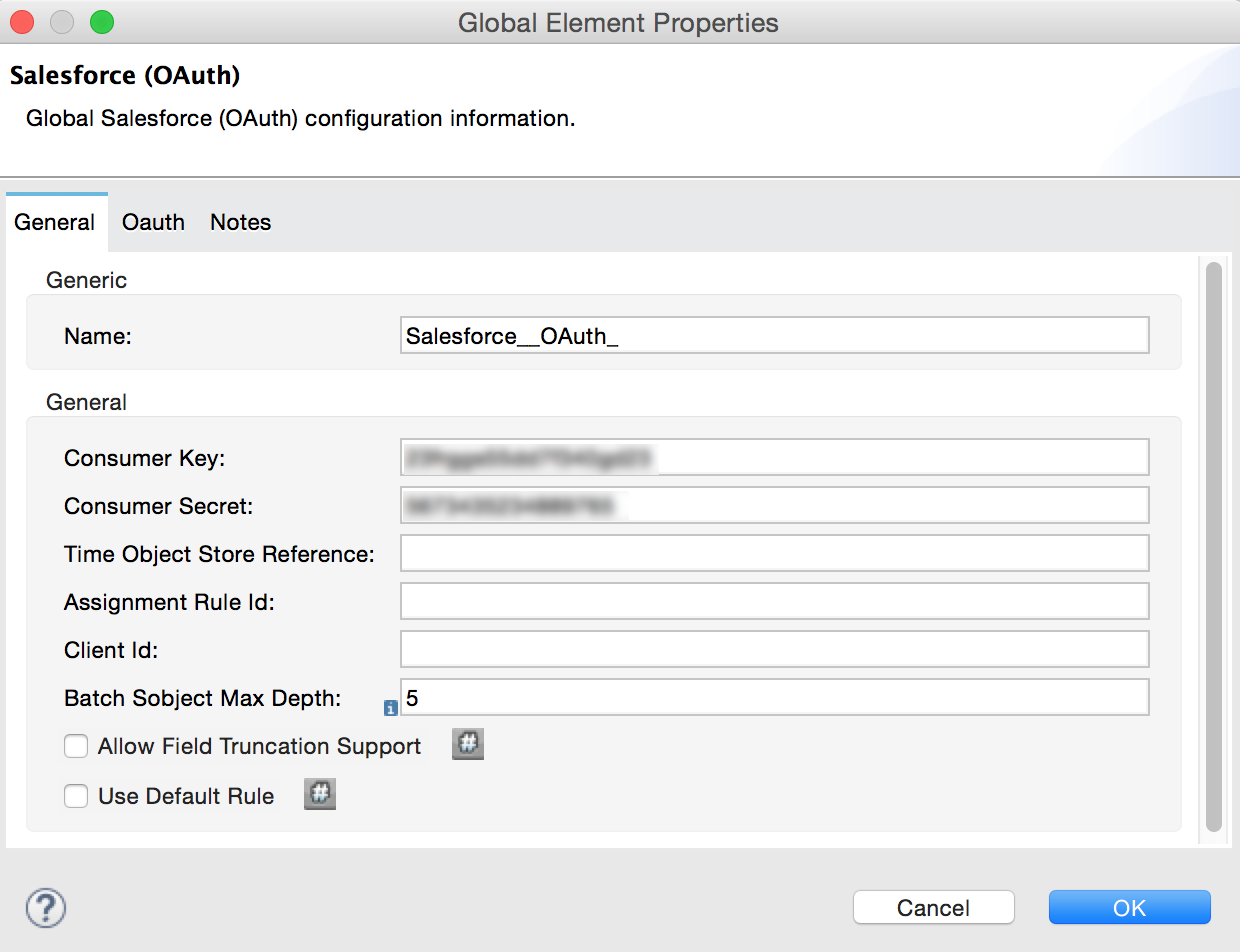
In the Global Element Properties panel, enter the Consumer Key and Consumer Secret with the information that the software service provider gave you.
-
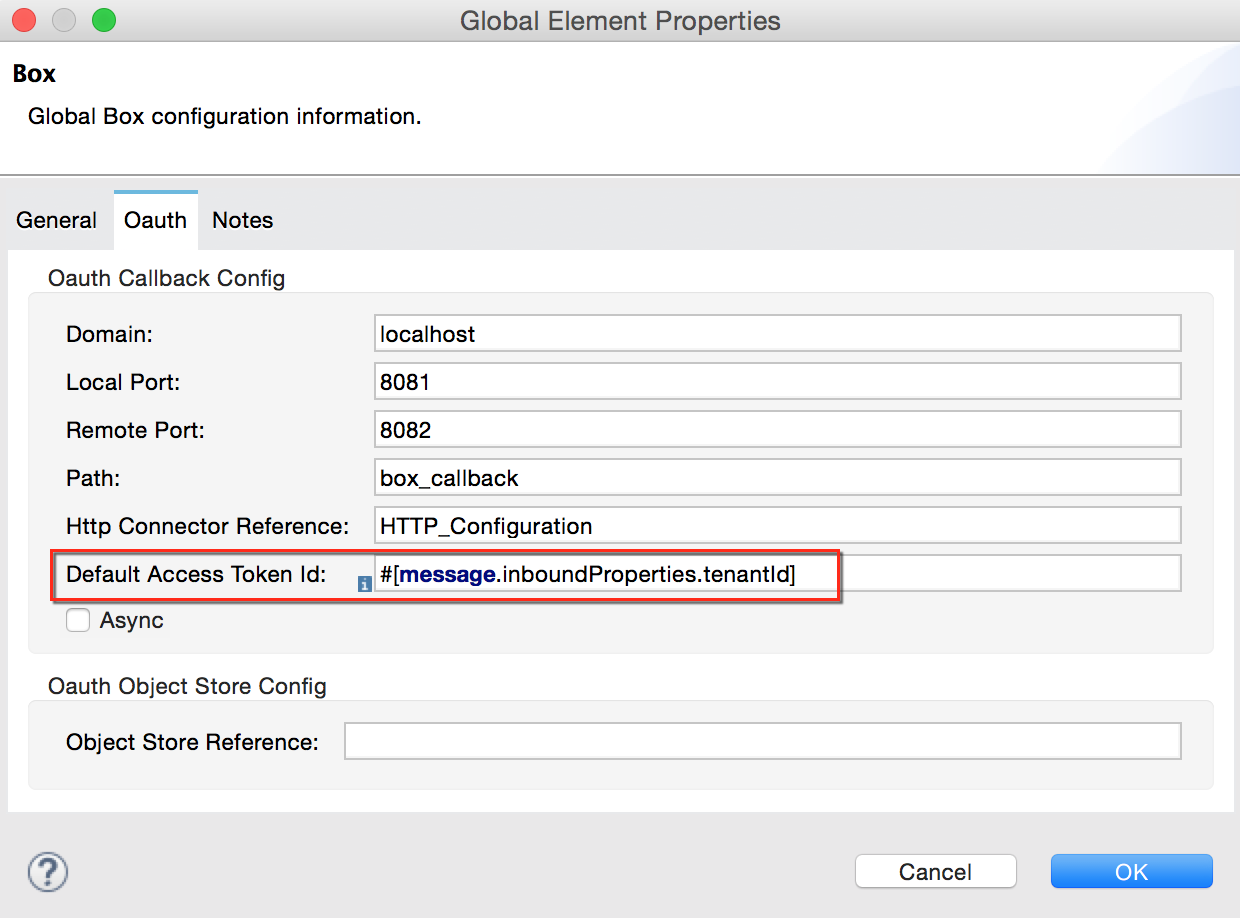
On the OAuth tab, enter the callback URL’s Domain , Port , and Path . The example below results in a callback URL of
http://localhost:8081/callback.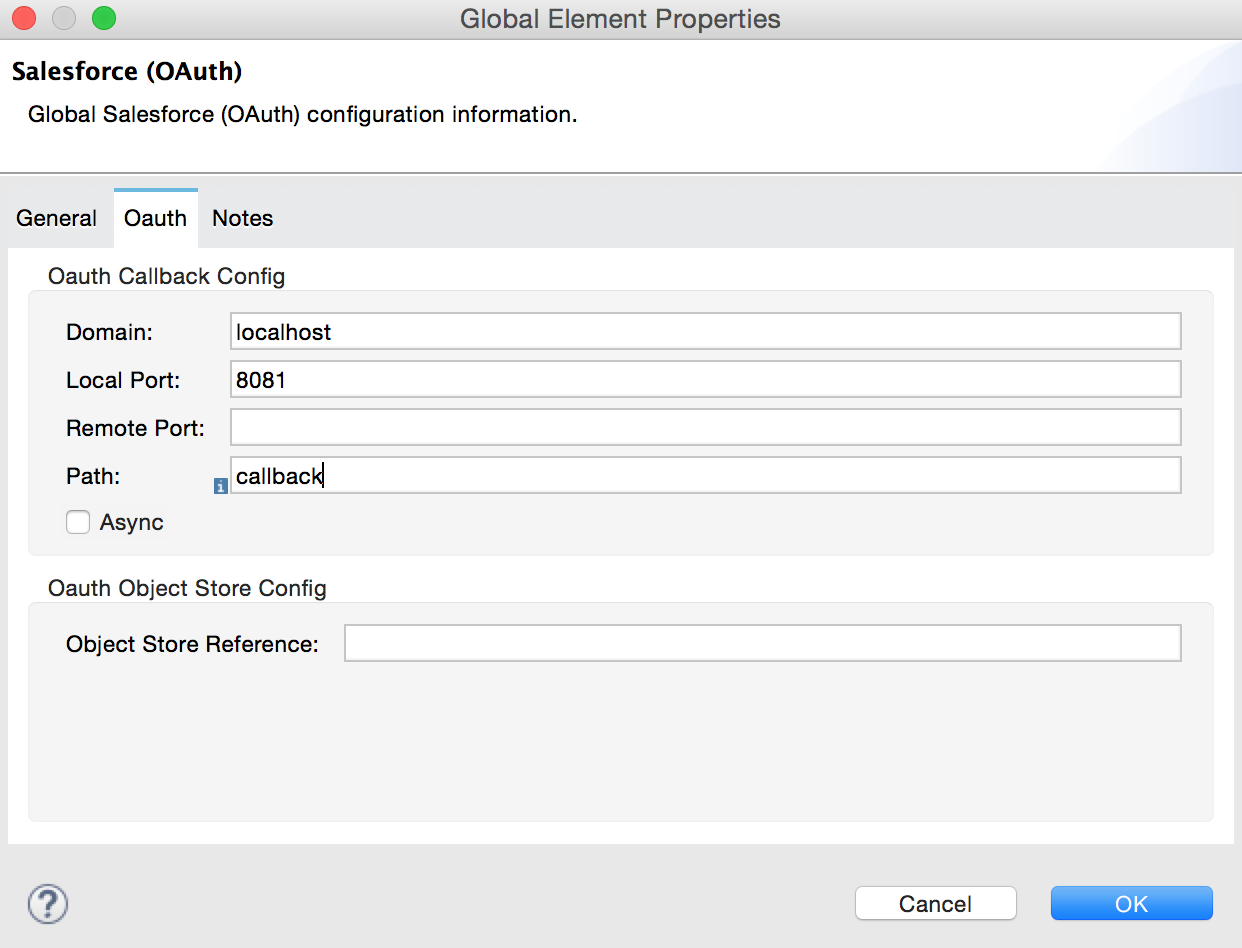
Field |
Description |
Domain |
Should be the domain assigned to the listener at the start of your OAuth callback flow. When in production, this is the domain on which your application is hosted. |
Local Port |
The port on which your authorization flow is hosted. This is the port configured on your HTTP listener, for example, |
Remote Port |
The domain and port of the listener at which your OAuth callback is hosted. |
Path |
The path of the listener at which your OAuth callback is hosted. |
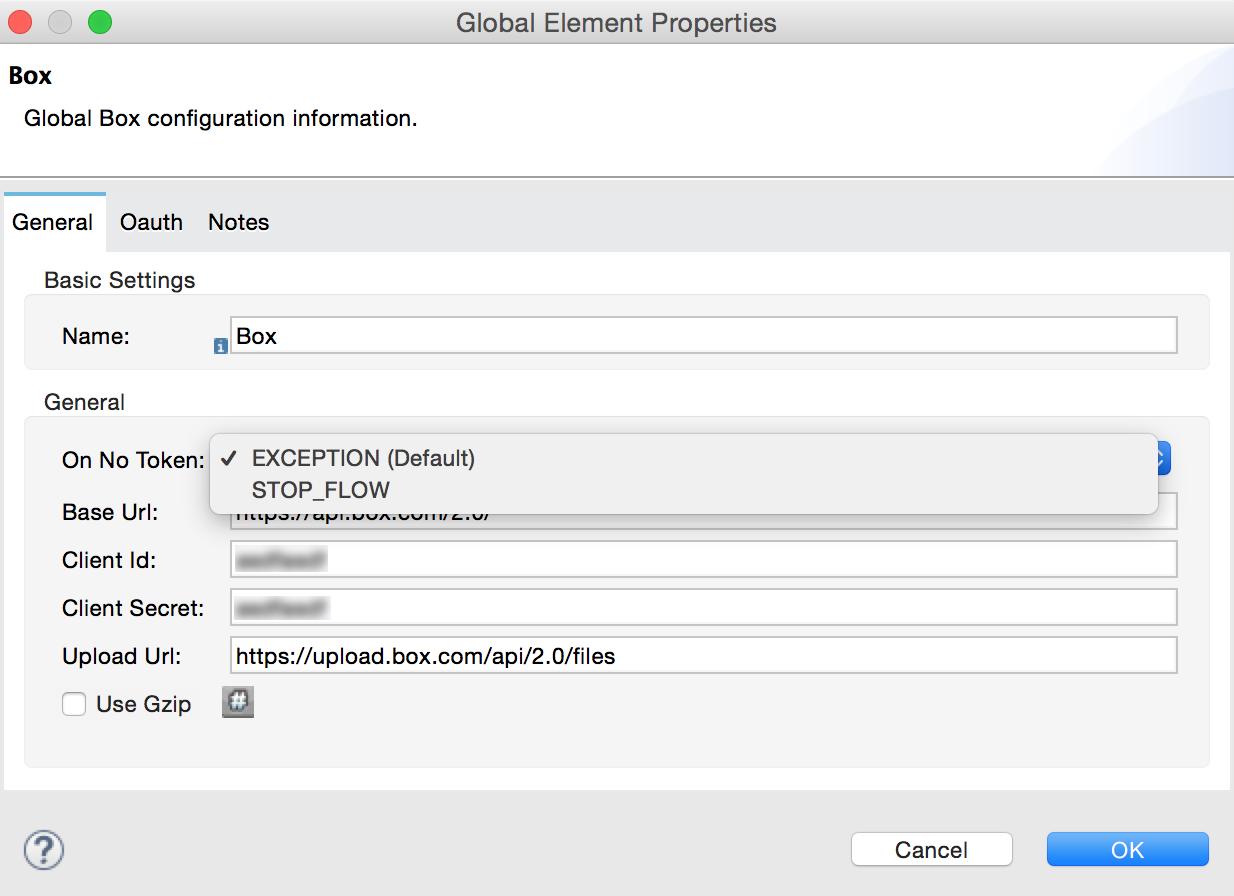
Controlling Flow Processing
You can define the behavior of a connector for situations when a user with no OAuth token attempts to utilize the service (that is, the user is not yet authenticated via OAuth). Use the On No Token field to select one of the following two options.
STOP_FLOW |
Behaving like a filter, this option kills flow execution . This choice is ideal for keeping log files light as it doesn’t create exceptions before you have had a chance to authorize your connector to access the OAuth provider. |
EXCEPTION |
(Default) Throws an exception advising the user that an OAuth token is required. |
XML Editor or Standalone
-
Configure a global Salesforce (OAuth) element according to the table below.
<sfdc:config-with-oauth name="salesforce" consumerKey="[insert key]" consumerSecret="[insert secret]" doc:name="Salesforce (OAuth)"> </sfdc:config-with-oauth>xmlGlobal Element sfdc:config-with-oauthAttribute Value name
name of the global elementconsumerKey
`consumer key as provided by service provider `
consumerSecret
`consumer secret as provided by service provider `
doc:name
Studio only. Name of the global element.
-
Add a child element to define the Callback URL. The example below results in a callback URL of
http://localhost:8081/callback.
Attribute |
Example Value |
Description |
domain |
|
|
The domain of the listener on your OAuth callback flow. When in production, this is the domain on which your application is hosted. |
localPort |
|
The port you configured on the listener of the authorization flow |
remotePort |
|
The port you configured on the listener of the OAuth callback. |
path |
|
The path of the listener at which your OAuth callback is hosted. |
Controlling Flow Processing
You can configure your connector to define the behavior of a connector when a user with no OAuth token attempts to utilize the service (i.e. the user is not yet authenticated via OAuth). Use the onNoToken attribute to define one of the following two options.
STOP_FLOW |
Behaving like a filter, this option kills flow execution. This choice is ideal for keeping log files light as it doesn’t create exceptions before you have had a chance to authorize your connector to access the OAuth provider. |
EXCEPTION |
(Default) Throws an exception advising the user that an OAuth token is required |
<sfdc:config-with-oauth name="salesforce" consumerKey="[insert key]" consumerSecret="[insert secret]" doc:name="Salesforce (OAuth)" onNoToken="[STOP_FLOW]">
<sfdc:oauth-callback-config domain="localhost" remotePort="8082" path="callback"/>
</sfdc:config-with-oauth>xml